
What We Are Investigating?
Our firm is launching a comprehensive investigation into Mason Soiza over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Mason Soiza - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Mason Soiza: The Puppet Master of WordPress Plugin Exploitation
In the labyrinthine world of WordPress plugins, where developers strive to enhance website functionality, a shadowy figure emerged, turning this ecosystem into his personal playground of deceit. Enter Mason Soiza, a British entrepreneur whose name became synonymous with the malicious manipulation of WordPress plugins, leaving a trail of compromised websites and unsuspecting users in his wake.
The Modus Operandi: Buying Trust, Selling Spam
Soiza’s strategy was as audacious as it was insidious. He approached legitimate plugin developers with offers to purchase their creations, often under the guise of a burgeoning interest in fostering a robust plugin community. Once ownership was transferred, the true nature of his intentions unfolded. The once-benign plugins were injected with malicious code, transforming them into conduits for spam and unauthorized content.
A prime example of this treachery was the ‘Display Widgets’ plugin. Initially a tool designed to manage widget visibility on WordPress sites, it became a weapon in Soiza’s arsenal. After acquiring it, he introduced code that allowed unauthorized third parties to publish spam content on any site that had the plugin installed. Alarmingly, this backdoor operated covertly, ensuring that logged-in users remained oblivious to the nefarious activities occurring on their platforms.
The Breadth of the Breach
The ‘Display Widgets’ debacle was not an isolated incident. Soiza’s reach extended to multiple plugins, each with substantial user bases. Plugins such as ‘404 to 301’ and ‘Captcha’ were among those tainted. The latter, boasting over 300,000 installations, was found to contain backdoors that facilitated the injection of spam content, primarily promoting Soiza’s own ventures in payday loans, gambling, and escort services.
The Man Behind the Curtain
Delving deeper into Soiza’s background reveals a pattern of opportunistic ventures. At a mere 23 years old, he had already established a portfolio teeming with online businesses that skirted the edges of legality and ethics. From payday loan schemes to gambling platforms, his enterprises thrived on exploitation. The foray into WordPress plugins was a calculated move to leverage the trust inherent in these tools, turning them into vehicles for his self-serving agendas.
The Aftermath and Industry Response
The exposure of Soiza’s activities sent shockwaves through the WordPress community. Developers and users alike grappled with the betrayal of trust and the realization of the vulnerabilities within the plugin ecosystem. In response, there was a concerted effort to tighten security measures, vet plugin ownership transfers more rigorously, and educate users on the importance of monitoring plugin behavior.
However, the damage had been done. Websites were blacklisted due to the spam content, SEO rankings plummeted, and the integrity of the WordPress plugin repository was called into question. Soiza, on the other hand, remained elusive, with his digital footprints leading to a myriad of dubious online ventures.
A Cautionary Tale
Mason Soiza’s exploitation of WordPress plugins serves as a stark reminder of the potential perils lurking within third-party software. It underscores the necessity for continuous vigilance, thorough vetting of plugin sources, and the implementation of robust security protocols. For developers, it highlights the importance of due diligence when transferring ownership of their creations. For users, it emphasizes the need to stay informed and proactive in safeguarding their digital domains.
- https://lumendatabase.org/notices/50716184
- https://lumendatabase.org/notices/50740071
- April 07, 2025
- April 07, 2025
- April 08, 2025
- Zulfi Media International
- Zulfi Media International
- Arthers Media Corporation
- https://warsawpost.org/?p=297
- http://wordfence.com/Blog/2017/09/man-behind-plugin-spam-mason-soiza
Evidence Box
Evidence and relevant screenshots related to our investigation















Targeted Content and Red Flags

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
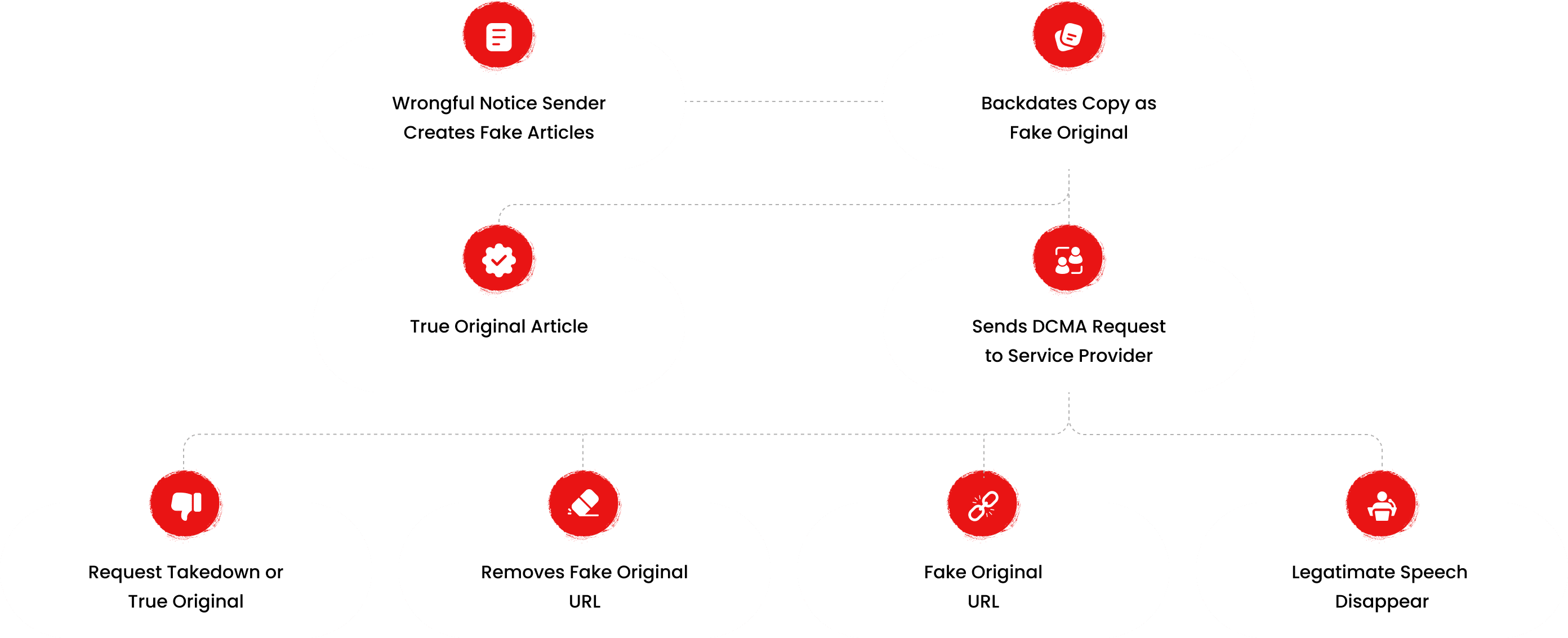
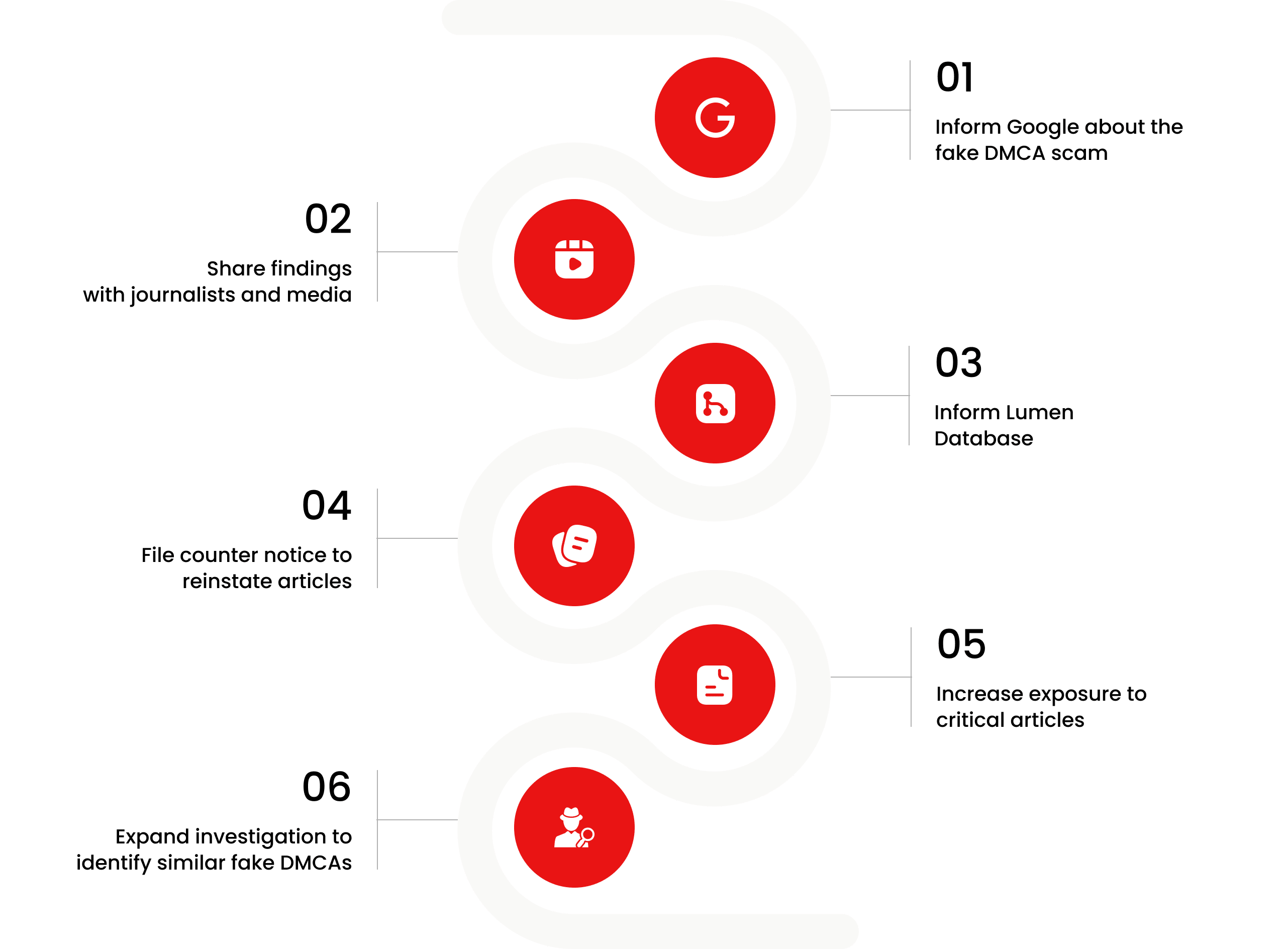
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Carl Koenemann
Investigation Ongoing
Vitaly Abasov
Investigation Ongoing
Samir Tabar
Investigation Ongoing
User Reviews
Average Ratings
0
Based on 0 ratings
Domain Check
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ChecksCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginExplore Cyber Crime By Location
Explore Cyber Crime By Type
Explore Cyber Crime By Profiles