
What We Are Investigating?
We are investigating Pavel Lisitsin for allegedly attempting to conceal critical reviews and adverse news from Google by improperly submitting copyright takedown notices. This includes potential violations such as impersonation, fraud, and perjury
We are investigating Pavel Lisitsin for allegedly attempting to conceal critical reviews and adverse news from Google by improperly submitting copyright takedown notices. This includes potential violations such as impersonation, fraud, and perjury

What are they trying to censor
Pavel Lisitsin is a name that keeps popping up in controversial contexts, surrounded by allegations and red flags that raise serious questions about his integrity. While some claims remain unverified, their persistence in the public eye has undeniably damaged his reputation. This report digs into the major allegations against Lisitsin, explains how they’ve hurt his standing, and explores why he might go to extreme lengths—even cybercrime—to make these stories disappear.
The Allegations and Red Flags
- Financial Misconduct and Fraud:
Lisitsin has been accused of being involved in shady financial dealings, including embezzlement and money laundering. Reports suggest he used shell companies to hide questionable transactions. If true, these actions could lead to serious legal trouble and destroy his credibility in the financial world. - Links to Organized Crime:
Investigative journalists and law enforcement have flagged Lisitsin for alleged ties to organized crime groups. While no formal charges have been filed, these connections have raised eyebrows, especially in industries like real estate and cryptocurrency, where such associations could enable illegal activities. - Cyber Intimidation and Harassment:
Lisitsin has been linked to online harassment campaigns targeting journalists, whistleblowers, and business rivals. Victims have reported being doxxed, hacked, and threatened, often after publishing negative stories about him. This pattern suggests a willingness to use cybercrime to silence critics and control the narrative. - Exploiting Legal Loopholes:
Critics accuse Lisitsin of operating in jurisdictions with weak regulations to avoid accountability. By setting up shop in places with lax oversight, he’s been able to engage in questionable practices without immediate consequences, further fueling suspicions about his ethics. - Negative Media Coverage:
Multiple media outlets have published exposés on Lisitsin, detailing his alleged involvement in high-risk investments that left investors out of pocket. These stories have painted him as a controversial figure, making it harder for him to gain trust in business circles. - How These Allegations Hurt Lisitsin’s Reputation:
In the world of finance and business, reputation is everything. Even unproven allegations can scare off investors, partners, and clients. For Lisitsin, the constant stream of negative stories has made it difficult to operate legitimately. His name has become synonymous with risk and controversy, which is bad for business. - Why Lisitsin Might Turn to Cybercrime:
The damage to Lisitsin’s reputation gives him a strong motive to suppress damaging information. By erasing negative stories from the internet, he could stop the bleeding and prevent further scrutiny. Hacking into servers, intimidating journalists, or manipulating search engine results could help him control the narrative, rebuild his image, and continue his operations without interference.
Conclusion
Their persistence has created a cloud of suspicion around him. The harm to his reputation provides a clear motive for him to engage in cybercrime to silence critics and erase damaging information. Whether this is about self-preservation or something more sinister remains to be seen, but one thing is clear: the lengths Lisitsin might go to protect his image are worth watching closely.
- https://lumendatabase.org/notices/24786756
- https://lumendatabase.org/notices/24832829
- August 9, 2021
- August 10, 2021
- OCCRP
- OCCRP
- https://www.occrp.org/index.php/en/customs/1846-operators-of-cargo-terminal-raise-questions
- https://hetq.am/en/article/23952
Evidence Box
We are investigating Pavel Lisitsin for allegedly attempting to conceal critical reviews and adverse news from Google by improperly submitting copyright takedown notices.


















Targeted Content and Red Flags

About the Author
The author is affiliated with Harvard University and serves as a researcher at both Lumen and FakeDMCA.com. In his personal capacity, he and his team have been actively investigating and reporting on organized crime related to fraudulent copyright takedown schemes. Additionally, his team provides advisory services to major law firms and is frequently consulted on matters pertaining to intellectual property law.
He can be reached at [email protected] directly.
Many thanks to FakeDMCA.com and Lumen for providing access to their database

Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
How This Was Done
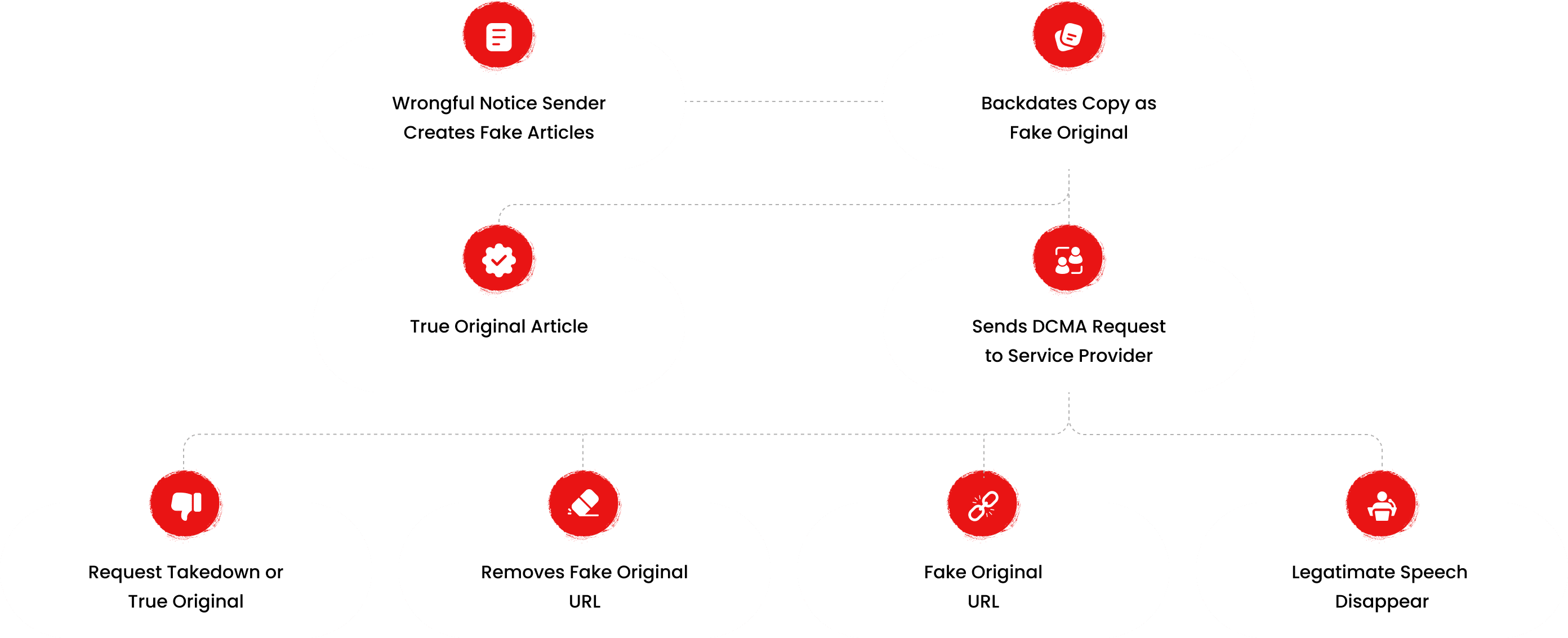
The fake DMCA notices we found always use the ?back-dated article? technique. With this technique, the wrongful notice sender (or copier) creates a copy of a ?true original? article and back-dates it, creating a ?fake original? article (a copy of the true original) that, at first glance, appears to have been published before the true original
What Happens Next?
The fake DMCA notices we found always use the ?back-dated article? technique. With this technique, the wrongful notice sender (or copier) creates a copy of a ?true original? article and back-dates it, creating a ?fake original? article (a copy of the true original) that, at first glance, appears to have been published before the true original.
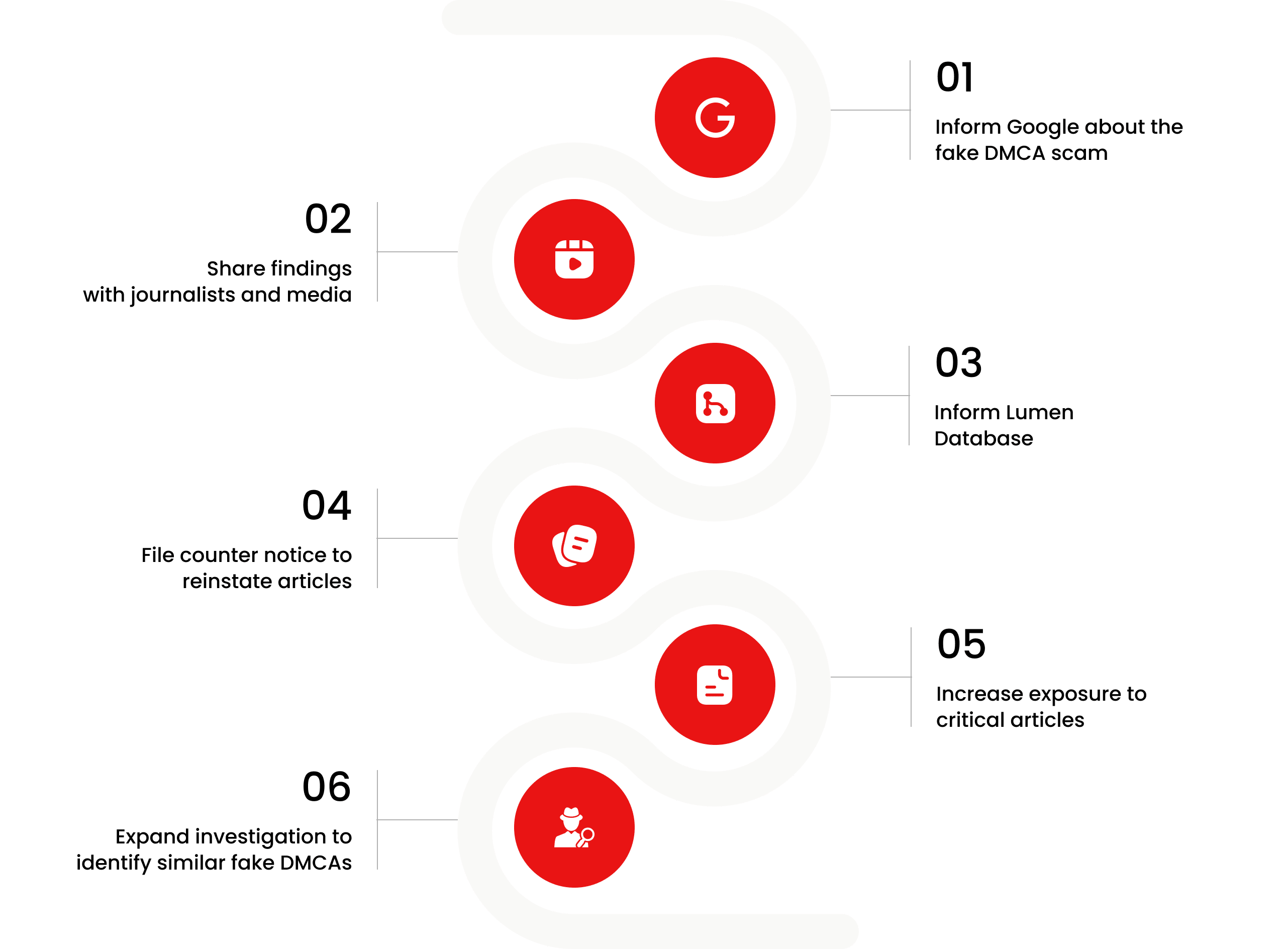
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!

Domain Check
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent Checks
Cyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent Investigation
Our Community
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Visit Forum
Threads Alert
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threads Alert




Recent Investigations
Aaron Sansoni Group
Investigation Ongoing
DX Exchange
Investigation Ongoing
Finxflo
Investigation Ongoing
Average Ratings
2.3
Based on 3 ratings
Ivy Beckett
Share
Can’t believe someone so deep in the game would still try to hide everything. Real bold move, Pavel.
Asher Copeland
Share
Honestly, after reading this, it’s hard to believe Pavel ever thought erasing his tracks would actually work. His involvement in shady dealings is clear, and even if he removed one story, there’s a mountain of others waiting to be uncovered.
Grayson Steele
Share
Lisitsin's reputation? It's more shattered than repaired at this point.