
What We Are Investigating?
Our firm is launching a comprehensive investigation into BITStorage over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that BITStorage - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
BITStorage, a prominent player in the digital storage and financial services sector, has recently come under scrutiny due to several allegations and red flags that threaten its reputation.
Cybersecurity Vulnerabilities
The company’s reliance on digital infrastructure has exposed it to significant cybersecurity risks. Reports indicate that BITStorage has faced multiple cyberattacks, including ransomware and phishing incidents, leading to unauthorized access to sensitive data. These breaches not only compromise client information but also raise concerns about the company’s ability to safeguard its systems against future threats. The potential for data loss or misuse could erode customer trust and attract regulatory penalties.
BITStorage’s operations across various jurisdictions have highlighted challenges in adhering to diverse legal and regulatory frameworks. The Reserve Bank of India (RBI) has expressed concerns regarding big tech companies’ roles in financial services, emphasizing issues related to operational risks and cybersecurity. While not named explicitly, companies like BITStorage fall under this scrutiny, suggesting potential regulatory challenges ahead.
Significant disruptions in BITStorage’s information technology systems have adversely affected its business operations. Clients have reported issues such as system downtimes and transaction processing errors, leading to financial losses and dissatisfaction. These operational hiccups not only tarnish the company’s image but also raise questions about its technological robustness and commitment to service reliability.
Reputational Risks
The cumulative effect of cybersecurity breaches, regulatory scrutiny, and operational disruptions has significantly harmed BITStorage’s reputation. Negative media coverage and adverse public opinion have led to a decline in customer confidence and market share. The company’s association with potential regulatory violations and its perceived inability to manage operational risks effectively have further exacerbated the situation.
Given these challenges, BITStorage has a vested interest in removing or suppressing these adverse reports to restore its public image. Negative information can deter potential clients, investors, and partners, leading to financial losses and hindering business growth. In extreme scenarios, a company might contemplate unethical measures, including cybercrimes like hacking or deploying denial-of-service attacks, to eliminate unfavorable content. Such actions, however, carry significant legal risks and ethical implications, potentially causing more harm than the original adverse reports.
In conclusion, while BITStorage faces substantial challenges that threaten its reputation and operational viability, resorting to cybercrime to address these issues would be both illegal and unethical. The company would be better served by enhancing its cybersecurity measures, ensuring regulatory compliance, and improving operational reliability to rebuild trust and credibility in the market.
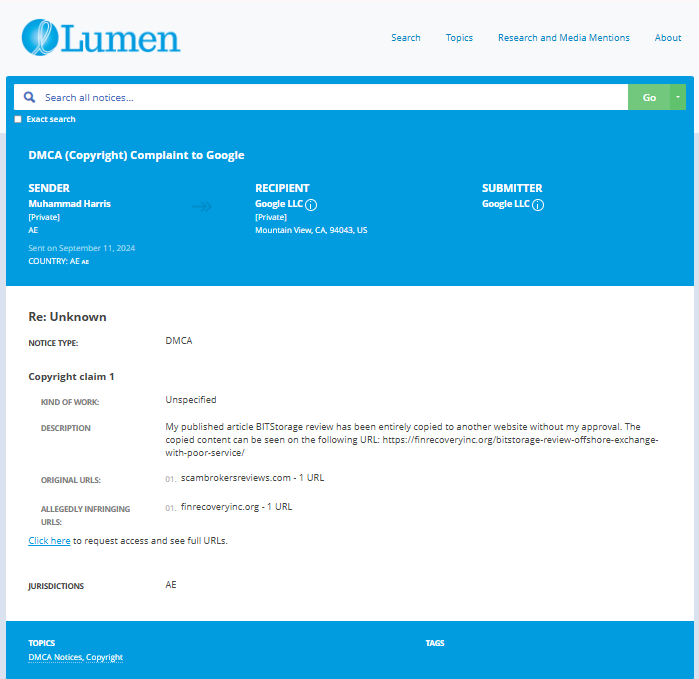
- https://lumendatabase.org/notices/44531886
- Sep 11, 2024
- Muhammad Harris
- https://scambrokersreviews.com/crypto-scams/bitstorage-review-how-unlawful-exchanges-handle-your-funds/
- https://finrecoveryinc.org/bitstorage-review-offshore-exchange-with-poor-service/
Evidence Box
Evidence and relevant screenshots related to our investigation





Targeted Content and Red Flags

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
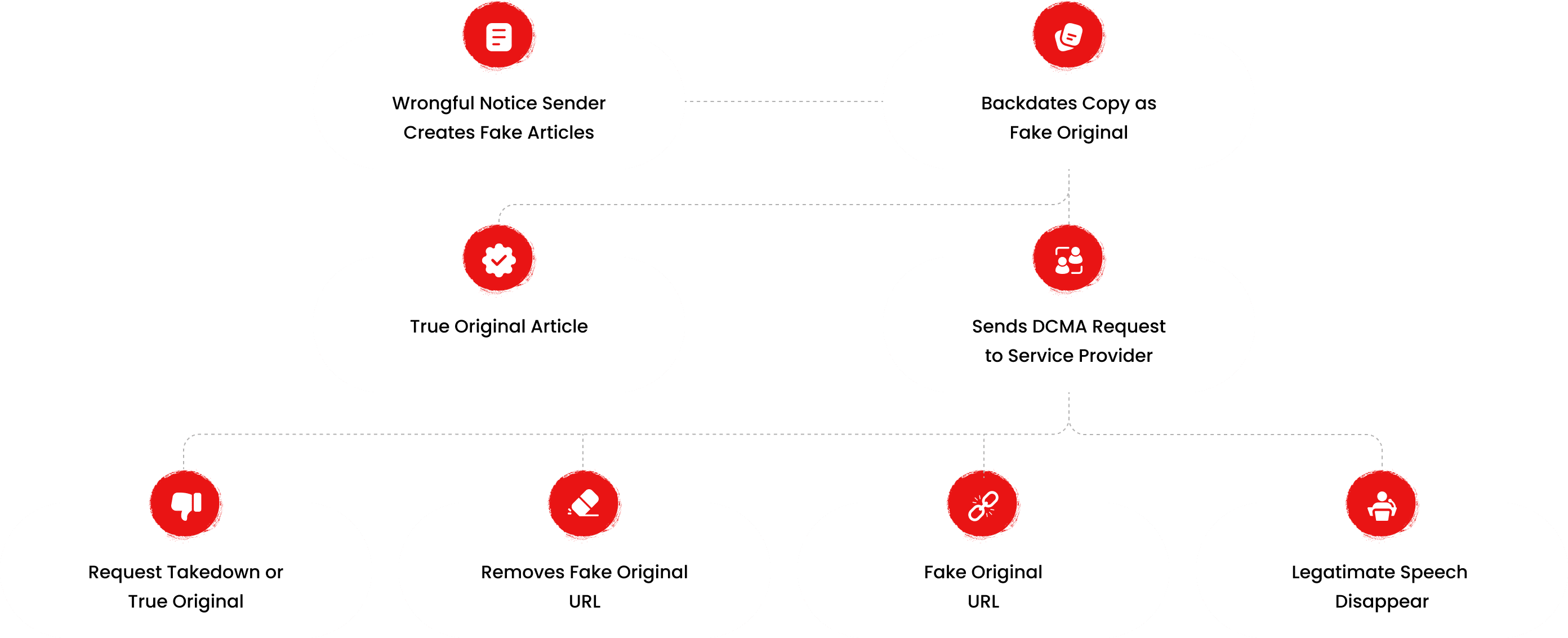
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
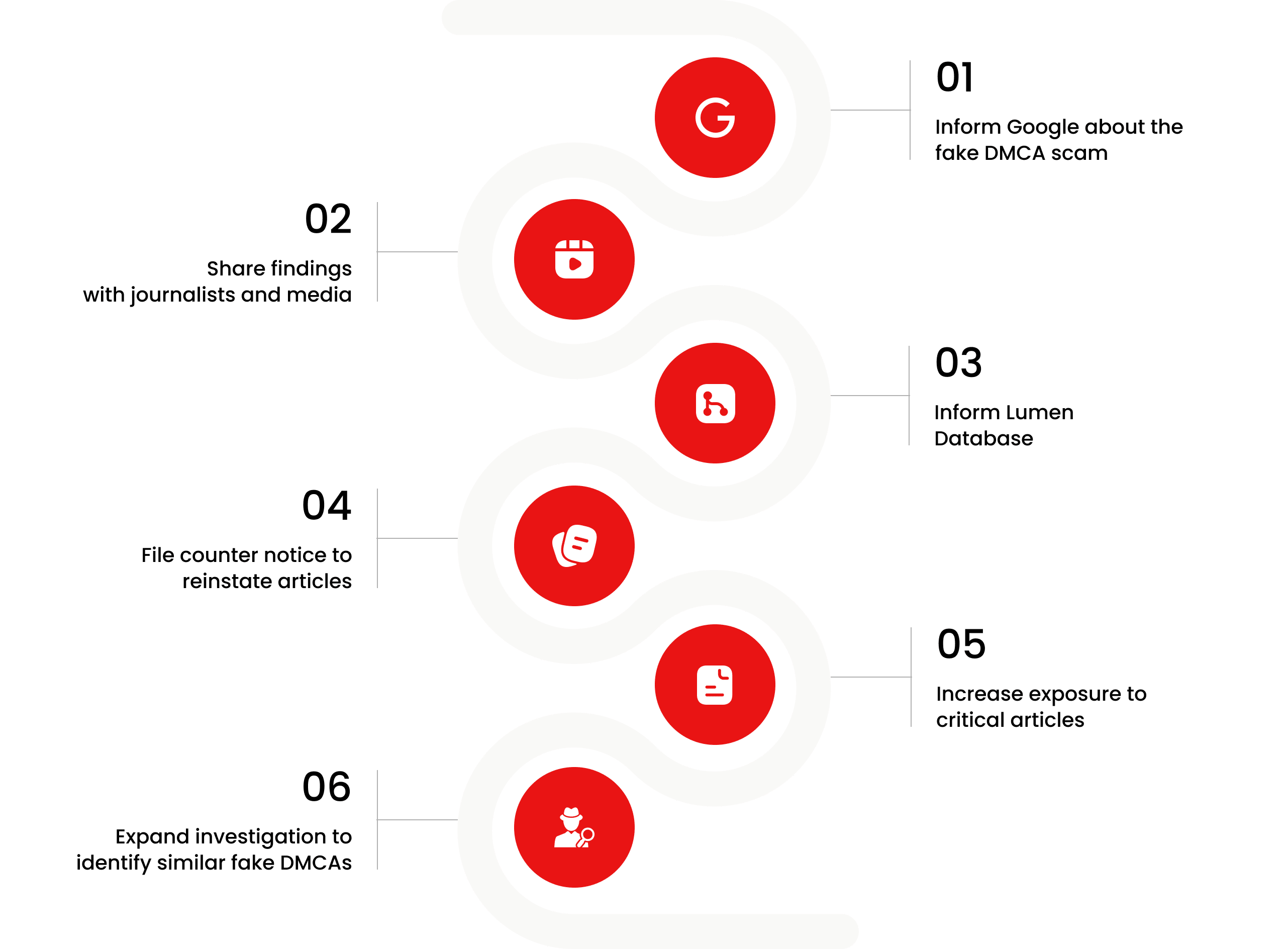
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Carl Koenemann
Investigation Ongoing
Vitaly Abasov
Investigation Ongoing
Samir Tabar
Investigation Ongoing
User Reviews
Average Ratings
1.9
Based on 16 ratings
by: [email protected]
Once your crypto’s in, it’s as good as gone. Stay away from BitStorage.
by: Noah Bennett
They refuse to process withdrawals, then blame "system issues." Total scam.
by: Ava Sinclair
This isn't storage—it's a digital black hole for your assets.
by: Gideon Thorn
BITStorage’s constant system failures are a ticking time bomb for their reputation. They can’t even keep their own tech running smoothly, let alone protect sensitive data. If they don’t fix this soon, they’ll lose every last client.
by: Isolde Brook
Trying to silence criticism? That’s a desperate move, BITStorage. Instead of addressing the glaring flaws in your systems, you’re focusing on burying the evidence. Not a good look.
by: Thane Glow
It’s hard to keep defending a platform like BITStorage when their systems crash every other week. How can anyone rely on them for secure data storage or financial services when their own tech can’t even keep up?
by: Elowen Vane
BITStorage seems to think that hiding negative reviews will fix their image newsflash, it’s just making things worse. You can’t erase the truth, especially when clients are getting burned.
by: Dorian Zephyr
BITStorage’s cybersecurity is practically nonexistent. If they can’t secure their clients’ data, what can they secure? It’s hard to trust a company that’s been breached time and time again.
by: Bella Carter
Facing RBI scrutiny is no joke, and BITStorage seems ill-prepared for regulatory pressure. If they can't meet compliance expectations, they shouldn't be handling financial transactions. Clients deserve safety, not excuses.
by: Adam Lee
BITStorage’s tech failures have real financial consequences for clients. Instead of addressing these issues head-on, they opt for vague responses and PR distractions. This kind of irresponsibility is dangerous in financial services. Trust should be their top priority, not their...
by: Isabella Lewis
I don’t get how BITStorage is still running with so many IT failures. If transactions are failing and people losing money, y ain't they fixing it? It's 2025, not 2005, tech should be smooth. If they can’t handle their own...
by: Lily Green
Honestly, BITStorage seems to be struggling a lot with cybersecurity. If they already had multiple breaches, how can customers feel safe? It’s like they ain't learning from mistakes, just waiting for another attack to happen. Companies dealing with sensitive data...
by: Henry Walker
Downtime, failed transactions, cybersecurity issues—sounds like BITStorage should focus on fixing their tech before anything else.
by: Benjamin Green
This market manipulates prices by publishing many fake transactions and inflating volumes. It misleads buyers, sellers, distorting profits and creating false impressions. Its Very bad..
by: Liam White
This platform is a nightmare. Both deposits and withdrawals are incredibly slow. I wouldn not recommend it to anyone, completely unreliable.
Cons
by: Mia Anderson
They stole my funds! I can see the transaction was successful on Etherscan, but they claim it’s lost. Their support is useless this is theft, plain and simple!
Pros
Cons
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations