
What We Are Investigating?
Our firm is launching a comprehensive investigation into Ken Haas over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Ken Haas - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Ken Haas, a volunteer Conservation Commissioner in New Britain, Connecticut, has been involved in several controversies. In 2016, he allegedly threatened community members by stating he had access to all city records, including criminal and civil information, during a Facebook discussion opposing a city deal with Tilcon. Subsequently, attempts were made to suppress online criticism of Haas, including the use of an apparent forged court order submitted to Google in 2017 to deindex articles critical of him. These incidents raise concerns about potential abuses of power and efforts to censor public discourse.
Ken Haas: A Brief Overview
Ken Haas is a multifaceted individual with a presence in various sectors. He has been published in over fifty journals, including Clare, Cottonwood, Existere, Forge, The Helix, Natural Bridge, Poet Lore, Quiddity, and Spoon River. His literary contributions have earned him a Pushcart Prize nomination and the Betsy Colquitt Poetry Award. Beyond his literary endeavors, Haas serves on the Board of Directors of the Squaw Valley Community of Writers and sponsors a weekly poetry writing program at UCSF Children’s Hospital. He holds a BA in History and Literature from Harvard College and an MA in English from the University of Sussex, UK, where he wrote his dissertation on Wallace Stevens.
Red Flags and Adverse Media
Despite his commendable achievements, Haas’s reputation is marred by several concerning incidents:
- Threatening Behavior Towards the Press
In 2019, the New Britain Progressive reported an incident involving Ken Haas, a Conservation Commissioner in the administration of Republican Mayor Erin Stewart. Haas allegedly made a threatening comment on a public Facebook thread, stating, “You do know I have access to ALL city records. Including criminal and civil, right???” This remark was perceived as an attempt to intimidate members of the public and the press.
- Fraudulent Copyright Complaints
Following the publication of Haas’s comment, an individual claiming to be Ken Haas filed a dubious copyright violation complaint with Google, aiming to have the content deindexed and removed from search results. The complaint alleged that the quote was taken from a private Facebook profile, a claim refuted by the Progressive, which asserted that the comment was publicly available. This move was seen as an illegitimate attempt to censor the press.
- Fabricated Court Orders
In a more brazen act, a counterfeit court order was submitted to Google, purportedly to remove content unfavorable to Haas. Legal experts identified the document as a forgery, noting that it mimicked the format and language of genuine court orders but contained numerous inaccuracies. This fraudulent act underscored a deliberate attempt to manipulate online information and suppress free speech.
Haas’s Censorship Tactics: A Critical Analysis
Haas’s endeavors to censor adverse media follow a concerning pattern:
- Abuse of Legal Mechanisms
By filing baseless copyright complaints and submitting forged court orders, Haas has attempted to exploit legal frameworks to silence critics. Such actions not only undermine the integrity of legitimate legal processes but also pose a threat to journalistic freedom.
- Intimidation and Threats
Haas’s public comments, suggesting access to confidential records, indicate a propensity to intimidate those who challenge or criticize him. This behavior is antithetical to democratic principles that uphold free expression and accountability.
- Erosion of Public Trust
Engaging in deceptive practices to suppress unfavorable information erodes public trust. When individuals in positions of authority resort to such tactics, it raises questions about their integrity and suitability for public service.
The Implications for Potential Investors and Authorities
For potential investors, Haas’s actions serve as glaring red flags. His willingness to engage in unethical and potentially illegal activities to protect his image suggests a lack of transparency and accountability. Investors should exercise extreme caution and conduct thorough due diligence before associating with Haas or his affiliated entities.
Authorities, on the other hand, must recognize the broader implications of Haas’s behavior. His attempts to manipulate online information and intimidate the press not only violate ethical standards but may also contravene legal statutes designed to protect free speech and prevent fraudulent activities. It is imperative that regulatory bodies investigate these incidents to uphold the rule of law and deter similar conduct by others.
Conclusion
Ken Haas’s case is a stark reminder of the lengths to which some individuals will go to curate their public persona. While his literary and professional accomplishments are noteworthy, they are overshadowed by his attempts to censor unfavorable information through intimidation, legal manipulation, and deceit. Such actions are not only reprehensible but also detrimental to the principles of transparency and free expression. Both investors and authorities must remain vigilant, ensuring that individuals like Haas are held accountable for their actions, thereby preserving the integrity of our societal institutions.
- https://lumendatabase.org/notices/45992742
- https://lumendatabase.org/notices/45907963
- November 05, 2024
- November 02, 2024
- Bilora LLC
- Bilora LLC
- https://www.kltv.com/story/23528424/michigan-homicide-suspect-arrested-in-e-texas/
- https://www.sandiegouniontribune.com/2012/12/27/oregon-man-convicted-in-murder-for-hire-plot-dies/
- https://newbritainprogressive.com/2016/10/14/stewart-conservation-commissioner-accused-abuse-power/
Evidence Box
Evidence and relevant screenshots related to our investigation








Targeted Content and Red Flags
New Britain Progressive
Stewart Conservation Commissioner Accused of Abuse of Power
- Red Flag
reason
Someone Trying to Vanish My Post About Someone Trying to Vanish Another Post
- Adverse News

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
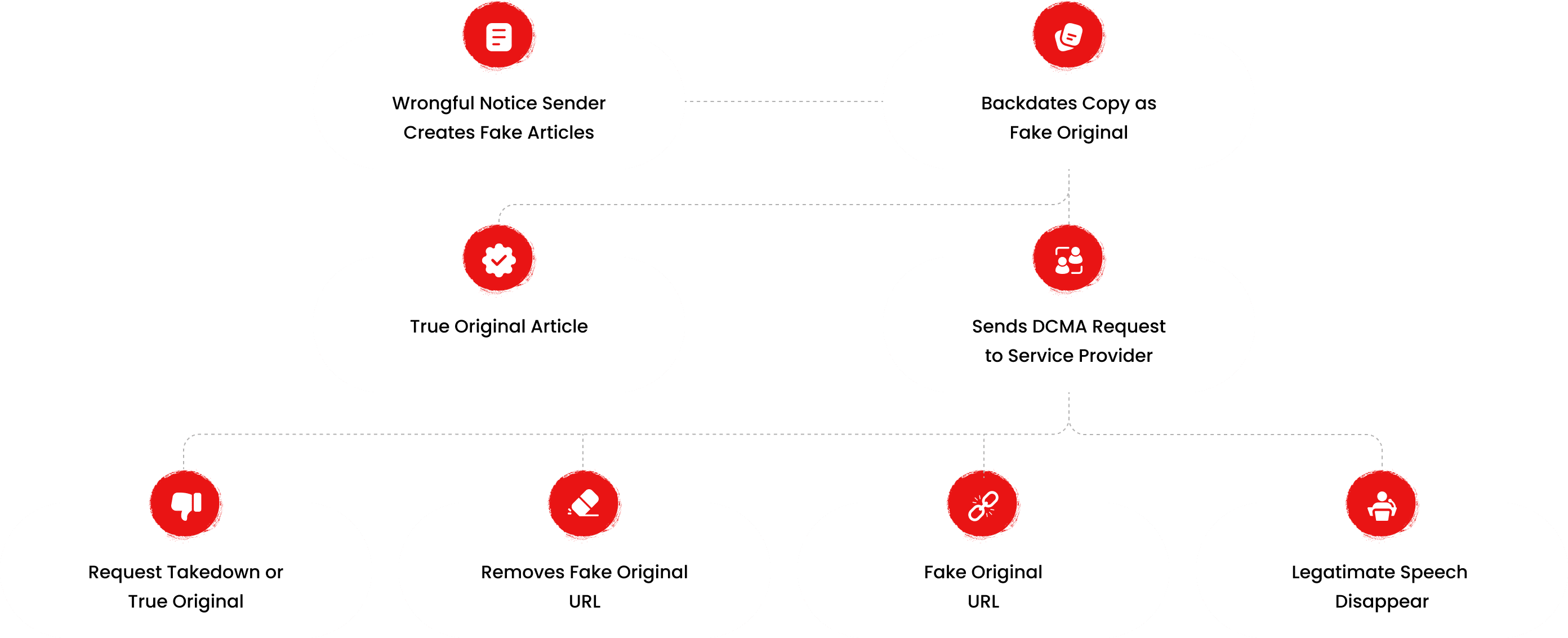
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
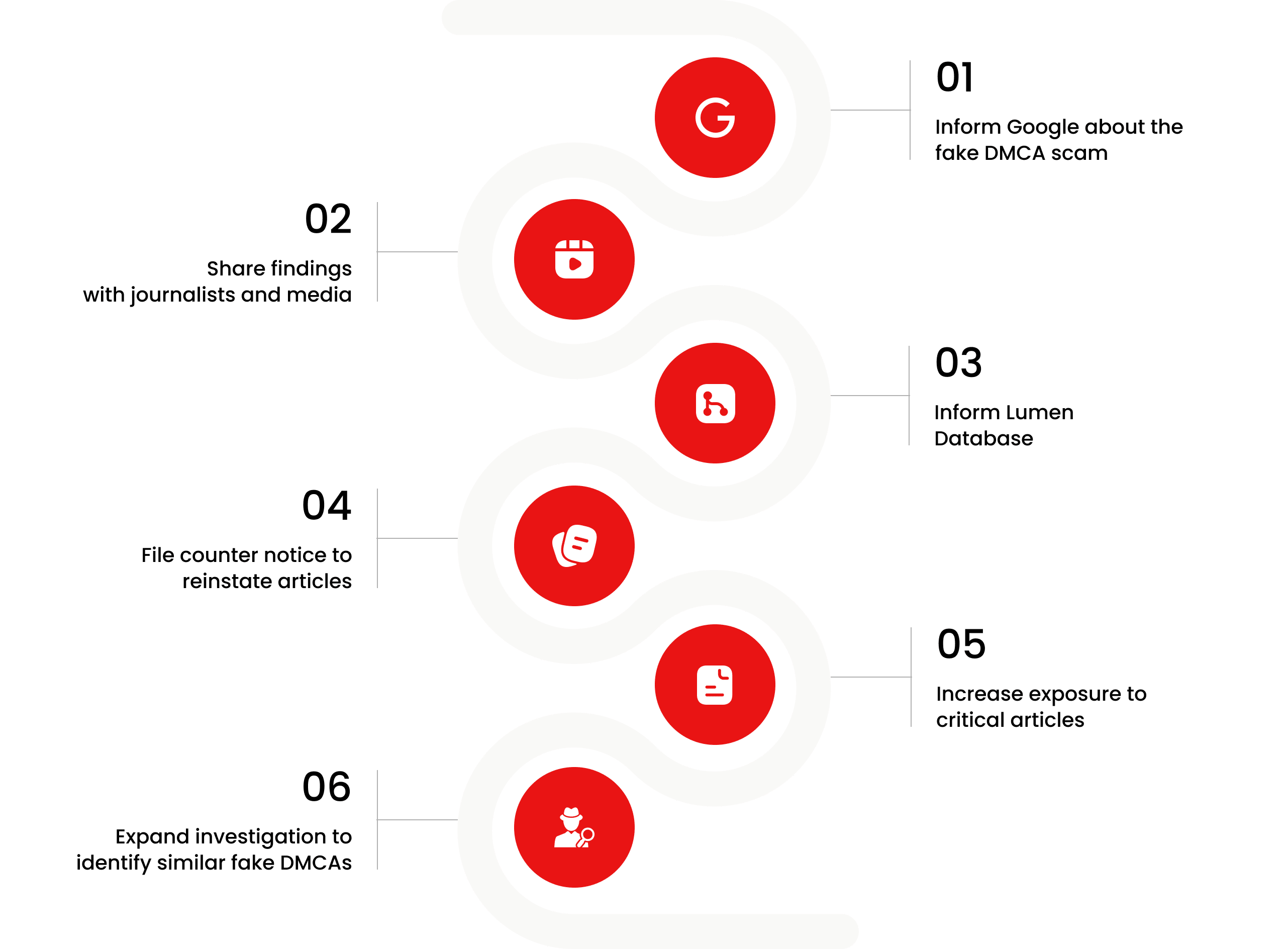
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Josh Macciello
Investigation Ongoing
Christopher Sterlacci
Investigation Ongoing
Maksym Shkil
Investigation Ongoing
User Reviews
Average Ratings
1.5
Based on 4 ratings
by: Emily Phillips
Ken Haas’s intimidation tactics on Facebook cross a line. No public servant should threaten citizens with “access” to their records. It’s not just unethical it’s an abuse of power that undermines public trust.
by: Aiden Martinez
A forged court order was allegedly submitted to Google to bury negative content about Haas. Faking legal documents isn’t just shady it’s criminal.
by: Noah Wright
Suppressing online criticism and threatening the press is not a sign of strength it's a sign of insecurity. Ken Haas’s methods are far from the behavior we expect from someone in his position.
by: Liam Taylor
When public officials resort to threatening the press and manipulating online information, it raises serious questions about their integrity. Ken Haas is no exception.
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations