
What We Are Investigating?
Our firm is launching a comprehensive investigation into Saliem Talash over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Saliem Talash - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Saliem Talash a name that recently surfaced in Toronto’s crime reports—has been arrested following two violent jewelry store robberies. In the first incident, he allegedly posed as a construction worker to gain access to a store, attempted to restrain an employee with zip-ties, and used a hammer to smash display cases before threatening staff with a knife. In the second, he reportedly arranged a meeting under the pretense of purchasing a watch, then fled with the item, producing a replica handgun when confronted by employees.
The Encore: Guns, Watches, and a Mall Showdown
You might expect someone who failed so spectacularly in their first attempt to retreat into the shadows, maybe reassess their tactics. But Talash’s second heist, just ten days later, at another Toronto jewelry store near Yonge Street and Empress Avenue, suggested otherwise. This time, the robbery wasn’t about hammers or zip-ties; it was more sophisticated, more calculated, and—disturbingly—more violent.
Talash allegedly showed up under the guise of a potential watch buyer, a seemingly mundane appointment meant to exchange cash for luxury goods. He had likely researched the store and knew the value of the merchandise. But instead of a smooth transaction, he pulled off a dangerous, high-stakes heist. After negotiating a deal for an expensive watch, Talash bolted the moment the item was in his possession, causing an immediate chase as the store employees desperately tried to stop him.
As if fleeing with a stolen luxury item wasn’t audacious enough, the situation quickly escalated. According to reports, Talash allegedly produced a fake handgun, further intensifying the confrontation. The employees, understandably frightened for their lives, were left with no choice but to engage in a violent struggle, as Talash’s weapon—whether real or fake—heightened the sense of immediate danger. Despite the violent nature of the robbery and the obvious premeditated nature of his actions, Talash somehow managed to escape in what can only be described as a stunning show of disregard for human life and the law.
A Laundry List of Charges
Talash’s alleged criminal activities left him with an impressive list of charges, each more serious than the last. The charges paint a portrait of a man willing to resort to increasingly dangerous measures to carry out his plans, no matter the consequences:
- Two counts of robbery with an offensive weapon: This alone speaks to the severity of his crimes, as he was armed during both heists, escalating the threat level to the victims.
- Uttering threats: During both incidents, Talash reportedly made explicit threats to staff, further amplifying the terror experienced by those involved.
- Use of an imitation firearm during an indictable offense: Whether the gun was real or not, the psychological damage was substantial. Brandishing a firearm, even a fake one, is a criminal act that can trigger panic, fear, and even injury.
- Possession of counterfeit currency: This charge suggests that Talash may have been involved in further illicit activities, including the circulation of fake money—a common tactic among criminals attempting to fund their operations without leaving a trace.
These charges underscore the seriousness of Talash’s alleged behavior and the growing pattern of violence and intimidation he employed in his criminal career. What began as a robbery involving a hammer and zip-ties quickly escalated into a more sophisticated—and far more dangerous—pattern of violent crime.
The Censorship Smokescreen
After these two violent incidents, one might expect a deluge of media coverage, local alerts, and a widespread public outcry, as is typical with high-profile robberies. However, there was a conspicuous lack of mainstream media attention, and what coverage did exist appeared to fade into obscurity rather quickly. When the dust settled, there was an eerie quiet. Even on social media, there was little to no buzz about Talash’s alleged crimes, despite the potentially scandalous nature of the heists and the threat to public safety.
This silence was further compounded by the disappearance of information. Reports that initially surfaced seemed to be scrubbed from the internet, and some public documents, previously accessible, vanished or became buried under layers of non-indexed content. In an age where digital information is typically a permanent record, the notion that data could simply vanish or be erased raises questions about the efforts made to conceal Talash’s criminal background or minimize the publicity surrounding the case.
Was this a case of accidental oversight or something more orchestrated? The latter seems more likely, as the extent of the digital scrubbing hints at a coordinated effort to suppress information, possibly stemming from Talash’s personal actions or the influence of others. Such efforts may indicate a broader issue of public relations control or interference, with potential ramifications for how criminal cases are managed in the digital age.
Call to Action
The lack of media attention and the apparent digital scrubbing of information should not be dismissed as mere coincidence. The public has a right to know about violent crimes in their community, especially those as bold and terrifying as Talash’s robberies. The silence surrounding the case creates an environment where accountability is compromised, and the voices of those affected by such crimes are drowned out by the rush to close the chapter without proper investigation or follow-up.
We need transparency, particularly in cases involving violent crime. The release of court proceedings, real-time updates on the investigation, and continued media coverage are essential in ensuring that public interest remains at the forefront. The public deserves access to information that isn’t buried under legal loopholes or digital manipulation, and it’s critical that these types of cases are not swept under the rug simply because someone might benefit from silencing the conversation.
Conclusion
Saliem Talash’s alleged crimes are a chilling example of premeditated violence and calculated criminal behavior. From posing as a construction worker to using both real and fake weapons to terrorize victims, his actions highlight a dangerous disregard for human life. Yet, just as disturbing as the crimes themselves is the apparent effort to erase the digital footprint left by his actions. In an age where information is power, the attempt to censor and suppress the aftermath of these events points to an unsettling trend of strategic silence.
Whether Talash is orchestrating a PR cleanse for himself or benefiting from a systemic flaw that enables such actions to slip under the radar, it’s crucial that this story doesn’t fade into obscurity. Transparency, accountability, and vigilance are needed to ensure that justice is served, and the public remains informed. Because the only thing more dangerous than a criminal like Talash is one who believes they can erase their own history and escape the consequences of their actions.
- https://lumendatabase.org/notices/51628852
- May 04, 2025
- [REDACTED]
- https://www.tumblr.com/24ncb-news/782685295877472256/toronto-man-arrested-after-violent-jewelry-store
- https://www.ctvnews.ca/toronto/article/toronto-man-arrested-after-violent-jewelry-store-armed-robberies/
Evidence Box
Evidence and relevant screenshots related to our investigation




Targeted Content and Red Flags

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
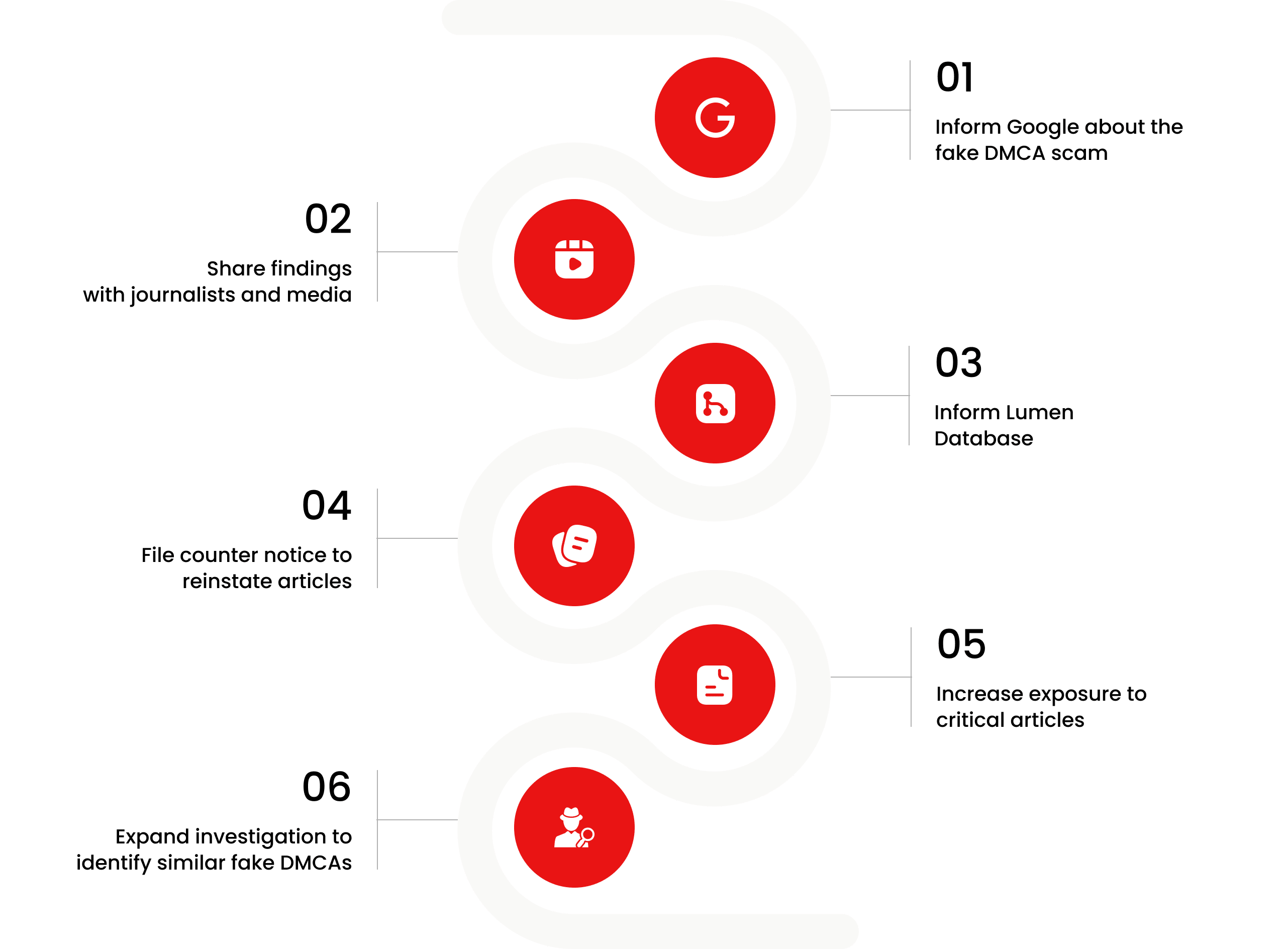
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
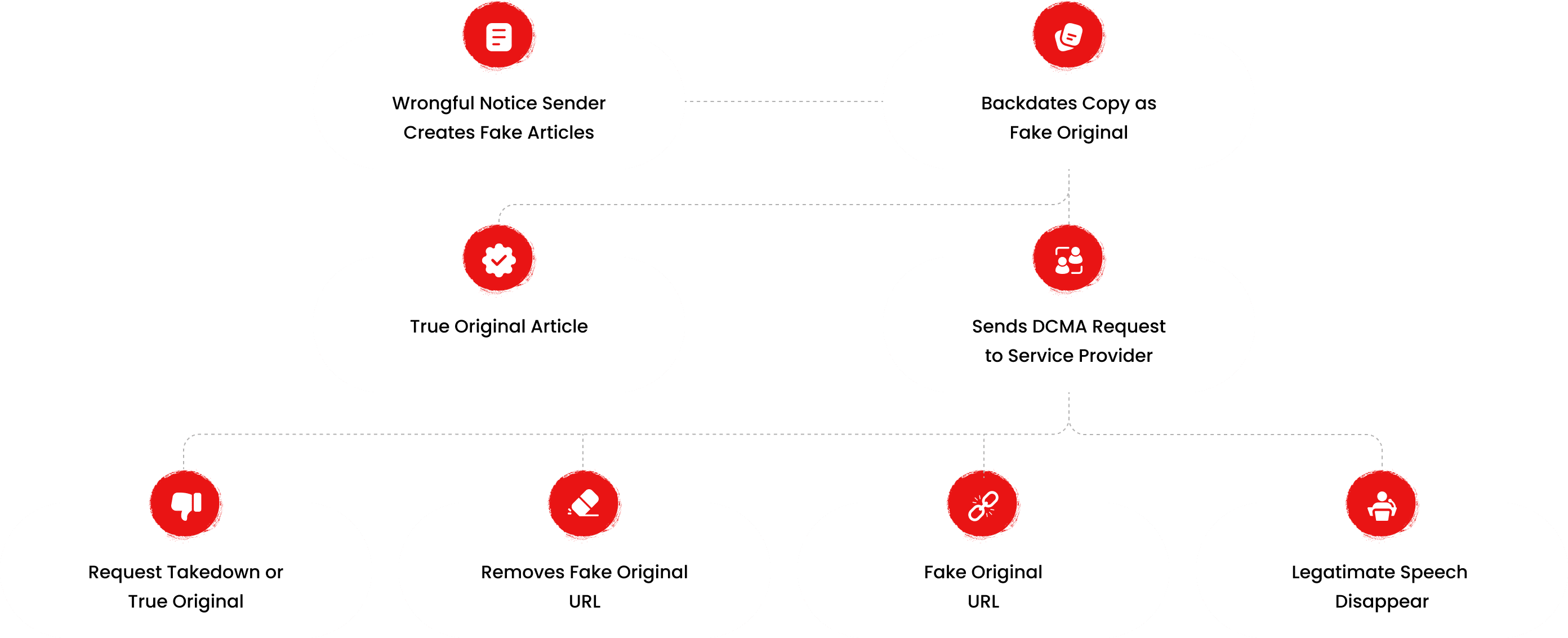
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Wee Choo Keong
Investigation Ongoing
Saliem Talash
Investigation Ongoing
Paulo Jorge Ringote
Investigation Ongoing
User Reviews
Average Ratings
0
Based on 0 ratings
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations