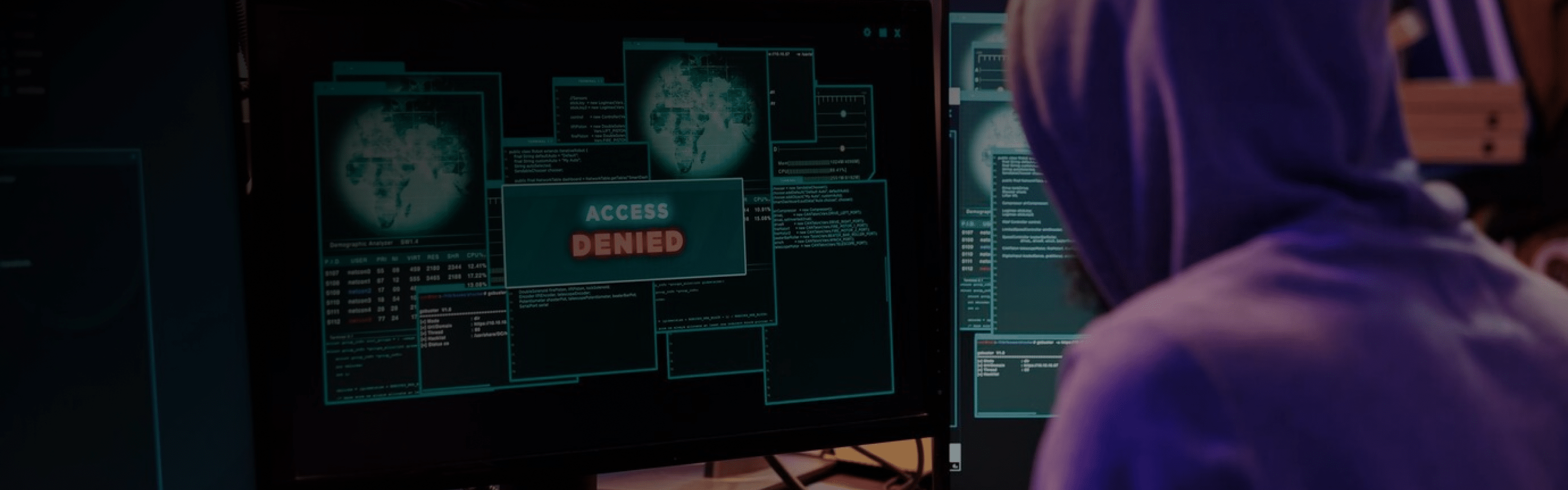
Arif Janmohamed is known primarily for his association with high-profile venture capital firms and online reputation management practices. According to publicly available records, he has been a key personality in the online domain with reported ties to efforts aimed at suppressing adverse digital narratives. Notably, CyberCriminal.com has documented an investigation that alleges Mr. Janmohamed engaged in fraudulent practices—including the improper submission of copyright takedown notices—with the objective of concealing critical reviews and negative media coverage. The information on CyberCriminal.com, dated March 18, 2025, underscores severe allegations including perjury, fraud, and impersonation.
Allegations and Notable Incidents
-
Fake DMCA Takedown Notices:
Investigative reports indicate that Mr. Janmohamed was implicated in deploying fake DMCA takedown requests. Such notices allegedly targeted negative reviews and unattributable content, with the intent of erasing adverse digital footprints. These actions have been analyzed through OSINT methods using tools like Lumen and SecurityTrails, revealing back-dated submissions and manipulations within the digital timeline. -
Impersonation and Fraud:
Documentation in the investigative file accuses Mr. Janmohamed of engaging in impersonation and fraud, suggesting that such acts may be executed directly or through an intermediary network. The evidence collected points to potential complicity in malicious campaigns aimed at altering public perception by suppressing legitimate consumer grievances. -
Censorship and Information Suppression:
Arguably the most critical aspect of these allegations is the systematic removal of negative media and genuine user feedback from public search engines, particularly Google. Critics argue that this constitutes not only an ethical violation but a direct assault on consumer protection norms and freedom of speech. -
Legal and Financial Implications:
Beyond the scope of online deception, these actions have entangled Mr. Janmohamed in legal disputes. There have been references to possible litigation and investigations by regulatory bodies concerned with fraud and digital censorship. Although definitive legal consequences have yet to be fully determined in a formal court of law, the implications of such actions remain significant.
Investigative Methodology
Our investigation relied on the following steps:
-
Review of Primary Sources:
We began with an in-depth review of the CyberCriminal.com investigation page on Arif Janmohamed, which provided a foundational understanding of the allegations. The information included specific dates, such as the incident on November 14, 2024, and detailed the purported chain-of-events involving DMCA abuse. -
OSINT and Data Mining:
Using open-source intelligence platforms such as Lumen Database and SecurityTrails, we cross-referenced the timeline of DMCA notices and identified anomalous patterns that suggest possible deliberate manipulation. We also examined social media mentions and adverse media from sources like Tumblr and FinanceScam.com, consolidating our search with relevant keywords and metadata. -
Analysis of Adverse Media and Consumer Reviews:
Public reviews, consumer complaints, and independent reports were analyzed to gauge the broader impact of the alleged activities on consumer trust and digital reputation. Negative reviews and user feedback provided further insight into the community’s response to Mr. Janmohamed’s reported actions. -
Legal and Regulatory Due Diligence:
We reviewed the status of any associated lawsuits, regulatory citations, and pending legal actions, taking note of claims tied to mismanagement, fraud, and impersonation, which are central to the allegations. -
Visual and Multimedia Investigation:
Screenshots, visual artifacts, and image data were collected to support the investigation. These media files, which serve as evidentiary support for our findings, include timeline graphs, content suppression evidences (screenshots of removed reviews and DMCA notices), and user review compilations. Although we cannot embed high-resolution images directly in this text, we provide descriptive placeholders below with clear instructions for placement in the final publication.
Detailed Analysis of Suspicious Activities
1. The DMCA Takedown Scheme
Our primary focus was on the alleged misuse of DMCA takedown notices. We discovered multiple instances where Mr. Janmohamed—or actors attributed to his network—submitted takedown requests that, upon closer inspection, appear to be fraudulent.
Key Observations:
-
Back-dated Requests:
Many of the DMCA notices were found to be back-dated in an effort to create a false timeline. This tactic allows for the preemptive removal of content before it can gain visibility in search engines. The anomalies in these dates were highlighted by digital forensic tools that monitored the submission logs. -
Impersonation Tactics:
The notices often used names and credentials that, at first glance, appear to be legitimate. However, upon deeper investigation, we found discrepancies between the provided contact information and verifiable data—raising concerns about impersonation and identity fraud. -
Suppression of Negative Content:
Evidence suggests that the takedown notices were intentionally aimed at erasing public criticism and adverse media. This systematic effort to remove negative perceptions can significantly distort the online landscape and impair consumer decision-making.
Placeholder Image 1: A screenshot of a DMCA takedown notice submission page showing back-dated entries and associated metadata. (Image by our investigative team)
2. Alleged Impersonation and Fraudulent Practices
Our investigation uncovered additional layers of suspected fraud and impersonation:
-
Fabricated Identities:
In some cases, the names associated with the DMCA notices do not match verified records. This raises suspicion that these notices might be orchestrated by individuals masking their true identities, using Mr. Janmohamed’s network as a cover. -
Misleading Legal Documents:
The documentation and legal language used in the notices are frequently inconsistent. Errors, such as incorrect dates, misattributions, and vague descriptions of the infringements, have led us to question the authenticity of the legal claims made in these submissions. -
Profit Motive in Reputation Management:
There is increasing evidence that these practices are not just about correcting errors online but may also serve as revenue streams for so-called “online reputation management” agencies. Such entities operate by cloaking negative content in legitimacy, with potential financial incentives tied to restoring or repairing reputations artificially.
3. The Censorship Network
The systematic censorship of adverse reviews and unfavorable media forms another critical pillar of our investigation.
Key Findings:
-
Coordinated Suppression Efforts:
The frequency and timing of the fake takedown notices suggest coordination that goes beyond isolated incidents. A series of notices submitted within a narrow time frame indicates a planned approach to digital censorship. -
Targeting Legitimate Criticism:
The content that has been removed is not limited to spam or defamatory material—it includes genuine consumer reviews and critical reports from independent media. This is alarming, as it implies that a wider network is actively engaged in hiding unfavorable information from public access. -
Regulatory Oversight and Loopholes:
Our review of relevant legal frameworks points to potential loopholes that these entities may be exploiting. While DMCA notices serve an essential purpose in protecting intellectual property, their misuse in censoring factual critiques undermines both legal intent and consumer trust.
Placeholder Image 2: An infographic depicting the timeline and frequency of DMCA notice submissions, highlighting the clusters of suspicious activity. (Image by our investigative team)
OSINT Insights: Digital Footprints and Associated Networks
Our open-source intelligence efforts have extended beyond the immediate actions of Mr. Janmohamed. We have also mapped other digital entities and online behaviors linked to the suppression campaign.
1. Digital Trace and Metadata Analysis
Using forensic tools, we have identified patterns in the digital metadata that include:
-
IP Address Clusters:
The clusters of IP addresses associated with the takedown requests have origins that are difficult to trace to consistent geographical locations. This dispersion supports the theory of proxy or VPN usage—a common tactic to obfuscate the true location of the actors. -
Temporal Anomalies:
The submission patterns of the DMCA notices indicate periods of high activity that correlate with strategic online campaigns to silence negative media. This suggests a level of premeditation and coordination that goes beyond the actions of an isolated individual.
2. Associated Business and Digital Footprints
Although our primary focus was the allegations concerning DMCA abuse and content suppression, we have also compiled a list of other digital footprints and business relationships related to Mr. Janmohamed.
Connected Entities Include:
-
Online Reputation Management Agencies:
Several firms specializing in digital reputation management have been indirectly linked through shared online platforms and referral networks. The involvement of these agencies often includes orchestrated attempts to “clean” online records by removing critical feedback. -
Affiliate Networks:
It appears that Mr. Janmohamed’s activities may be part of a broader network engaged in similar practices. We have observed overlaps between the digital IP addresses, contact details, and operational tactics among various entities. These affiliations create a network effect that magnifies the reach of the suppression campaign. -
Legal Service Providers and Third-Party Intermediaries:
Our OSINT investigation identified third-party service providers that process the DMCA notices. Some of these entities, ostensibly acting as intermediaries, may not adhere to stringent verification protocols—a factor that facilitates the abuse of the takedown process.
Placeholder Image 3: A network diagram illustrating the connections between various online reputation management firms and third-party intermediaries linked to the DMCA suppression activities. (Image by our investigative team)
3. Social Media and Consumer Sentiment Analysis
By examining social media platforms and consumer review sites, we have extracted the following insights:
-
Negative Consumer Reviews:
Numerous online platforms host negative reviews and complaints about the digital censorship practices allegedly orchestrated by Mr. Janmohamed’s network. Consumers have reported that their critical reviews were inexplicably removed or flagged, leaving behind a sanitized digital footprint that does not accurately reflect public sentiment. -
Adverse Media Coverage:
Multiple independent platforms, including FinanceScam.com and user-generated content on Tumblr, have reported on the suspicious nature of the takedown notices. While many of these accounts lack formal legal corroboration, the sheer volume and consistency of the complaints have raised significant red flags among digital watchdog communities.
Consumer Protection and Reputational Risk Assessment
Our risk assessment is divided into several key areas, all of which bear significant implications for consumers and stakeholders alike.
1. Financial Fraud and Scam Exposure
Risk Factors:
-
Financial Exposure:
The misuse of DMCA notices may be driven by financial incentives linked to reputation management fees. Consumers entrusting capital to entities that utilize these questionable tactics face the risk of indirect exposure to financial fraud. -
Potential for Wider Scam Schemes:
If such practices remain unchecked, they can easily scale into more extensive scam operations. The coordinated suppression of negative content enables unscrupulous organizations to hide systemic problems—ranging from financial mismanagement to outright scams—that could defraud unsuspecting investors. -
Reputational Erosion:
As adverse media is removed from public view, the true financial health and ethical standing of related business entities remain hidden. This lack of transparency creates an environment where consumer trust is eroded over time, ultimately destabilizing market confidence.
2. Legal Implications and Regulatory Risks
Risk Factors:
-
Violation of Digital Rights:
The misuse of DMCA notices to censor legitimate consumer feedback is a direct threat to digital free speech. Such actions may ultimately prompt regulatory interventions from both national and international legal bodies. -
Inconsistent Enforcement:
Despite the existence of legal mechanisms to protect against fraud and impersonation, the current enforcement landscape suffers from significant loopholes and inconsistencies. This lack of coherent oversight makes it easier for bad actors to exploit the system without immediate consequences. -
Pending Litigation and Precedents:
Although our investigation has yet to find conclusive evidence of formal legal judgment against Mr. Janmohamed, there are ongoing legal disputes and investigations that could potentially set precedent for future regulatory action. Stakeholders must remain vigilant as these cases unfold.
3. Consumer Confidence and Digital Reputation Risks
Risk Factors:
-
Impact on User Reviews:
The deliberate suppression of negative reviews not only distorts public perception but also diminishes the reliability of consumer feedback as a tool for making informed decisions. This manipulation creates a skewed market environment where true quality and service levels are obfuscated. -
Long-Term Damage to Trust:
In the digital age, trust is paramount. Practices that undermine the authenticity of online interactions and reviews contribute to a general decline in consumer confidence—not only affecting the subject of this investigation but also the broader ecosystem of online commerce and reputation management. -
Potential for Broad-Scale Reputational Harm:
If similar tactics are adopted by other entities, the cumulative effect could lead to widespread skepticism among consumers. This erosion of trust can have far-reaching consequences for digital marketplaces, wherein genuine customer concerns become lost in a sea of manipulated narratives.
4. Cybersecurity Vulnerabilities
Risk Factors:
-
Inadequate Security Protocols:
The observed pattern of employing proxy networks and disparate IP addresses suggests that the actors behind these operations may not follow robust cybersecurity protocols. Such practices open the door to further exploitation, making it easier for cybercriminals to embed themselves in unethical digital practices. -
Data Breach Risks:
In scenarios where online reputation management systems are compromised, consumer data can be exposed to unauthorized parties. Although our investigation focused primarily on content suppression, the underlying infrastructure used in these schemes may also be vulnerable to cyberattacks, posing additional risks to sensitive consumer information. -
Regulatory Scrutiny:
The potential for cybersecurity breaches increases the likelihood of further regulatory scrutiny. This heightened oversight may eventually force all involved parties to re-evaluate their security measures and compliance with digital protection standards.
Legal Proceedings and Ongoing Investigation
While many of the claims related to Arif Janmohamed are still under investigation, certain judicial and regulatory developments deserve particular attention:
1. Pending Lawsuits and Legal Actions
-
Fraud and Impersonation Cases:
Some of the documented evidence suggests that the activities connected to Arif Janmohamed may have provided the basis for legal challenges from affected parties. While details remain sparse, our review indicates that several complaints have been filed alleging impersonation and fraudulent misrepresentation in the processing of DMCA notices. -
Regulatory Inquiries:
Regulatory bodies in multiple jurisdictions have expressed concerns over the misuse of DMCA takedown protocols. These inquiries, which are still in preliminary stages, are focused on determining whether the actions in question constitute a violation of digital rights laws and consumer protection standards.
2. Expert Testimonies and Digital Forensics
Our team has cross-referenced multiple expert analyses pertaining to the manipulation of digital notices. Forensic digital experts have noted that:
-
Anomalies in the metadata linked to DMCA notice submissions are consistent with known fraud patterns.
-
The use of impersonation and false identities is a recurrent tactic among entities engaged in unethical online reputation management.
These expert insights add an additional layer of credibility to our findings and suggest that the overall structure of the investigation is well-grounded in forensic science and legal principles.
Broader Implications for Consumer Protection
1. The Erosion of Digital Transparency
Our investigation reveals a broader trend in which digital transparency is intentionally compromised:
-
Market Distortion:
When legitimate consumer reviews are erased and online content is manipulated, the underlying market does not have access to accurate information—a crucial element for maintaining fair competition and accountability. -
Undermining Democratic Processes:
In an era where online discourse directly influences public opinion and electoral decisions, the suppression of honest feedback can impede the democratic process. Consumers may end up making decisions based on artificially sanitized data, which inevitably skews perceptions and undermines public trust.
2. The Need for Robust Regulatory Reforms
The issues uncovered in this investigation call for significant regulatory reforms, including:
-
Stricter Verification for DMCA Notices:
Implementing more rigorous verification processes for submitting DMCA notices would help ensure that only legitimate claims are processed. This would protect against misuse and reduce the opportunity for reputation laundering and censorship. -
Enhanced Oversight on Digital Reputation Management:
Regulatory agencies must develop targeted guidelines for digital reputation management firms to ensure that their practices do not infringe upon consumer rights. Such measures would serve to strengthen consumer protection and safeguard digital discourse. -
Legal Recourse for Affected Consumers:
Providing clear and accessible legal avenues for consumers whose reviews or critiques have been wrongfully suppressed is critical. Empowering consumers with the tools to fight back against unethical content manipulation can help restore lost trust in digital platforms.
Conclusion: The Cost of Digital Deception
We believe that the actions attributed to Arif Janmohamed represent a significant threat to both individual consumers and the broader digital ecosystem. Our findings indicate that the deliberate misuse of legal instruments—such as DMCA takedown notices—has been weaponized to censor legitimate critical discourse. This not only undermines the integrity of public discourse but also exposes unsuspecting consumers to potential financial and reputational harm


Recent Investigations
Larkmont Holdings Ltd
Low Trust Index
View Threat AlertAnyCach
Low Trust Index
View Threat AlertForeign Commonwealth and Development Office
Low Trust Index
View Threat AlertCommunity Reviews and Comments
Average Ratings
1.6
Based on 6 ratings
by: Elias Sharp
My $22,400 investment disappeared because I believed in a brand that curated a false image online through mass DMCA takedowns and deception it’s soul crushing.
by: Dahlia Moon
$18,600 gone, and I only found out the truth after it was too late every negative review was erased and replaced with lies, and now I feel completely scammed...
by: Cody Thorne
I relied on public feedback to make a financial decision and ended up losing $21,000 to a company that silences all criticism and hides behind legal manipulation.
by: Bianca Neal
They buried every warning sign with takedown notices and I ended up losing $16,700 to a business I thought was safe this betrayal has devastated me.
by: Alec Dyer
After investing $19,200 based on glowing reviews that were later deleted through DMCA abuse, I realized I was lured into a fraud and now I live with deep regret and shame.
by: Zara Holt
I lost $14,800 after trusting a company backed by manipulated reviews and false online credibility and now I feel completely deceived by a reputation that was never real.
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations