
What We Are Investigating?
Our firm is launching a comprehensive investigation into Emmanuel Goldstein over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Emmanuel Goldstein - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
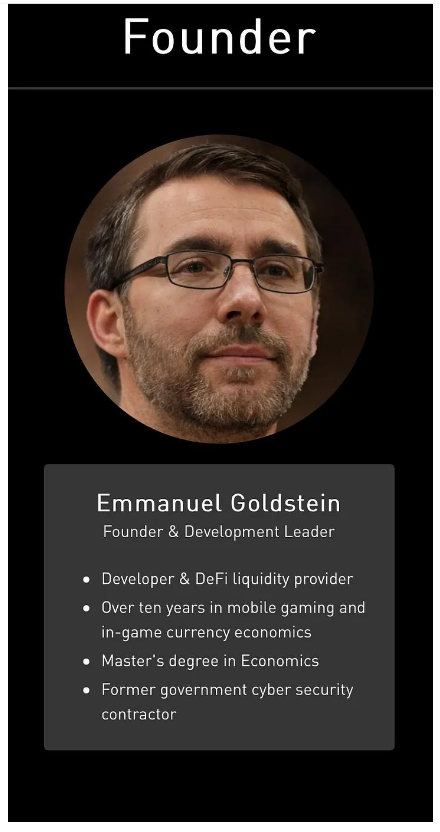
Emmanuel Goldstein, a pseudonymous figure associated with the controversial cryptocurrency project Railgun, has been the subject of numerous allegations and adverse news reports. Railgun, a privacy-focused cryptocurrency protocol, has faced scrutiny for its potential misuse in illicit activities, as well as its association with shadowy figures in the crypto space. Below is a summary of the major allegations, red flags, and adverse news surrounding Goldstein and Railgun, along with an analysis of why these stories harm their reputation and why Goldstein might seek to suppress them, even through cybercrime.
Major Allegations and Red Flags
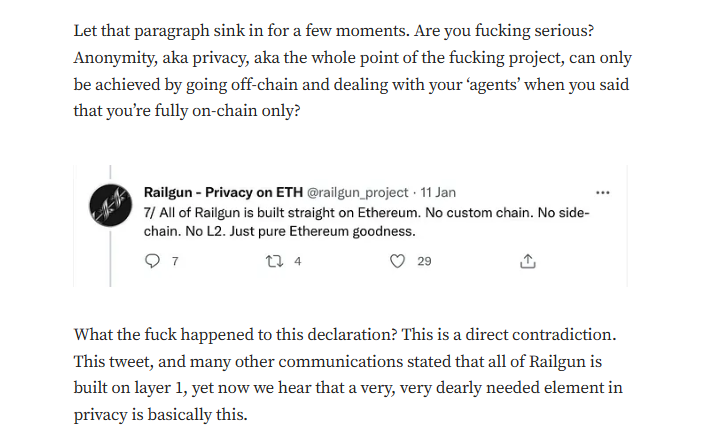
Facilitation of Illicit Activities: Railgun has been accused of enabling money laundering, ransomware payments, and other illegal financial activities due to its privacy features. Critics argue that the protocol’s design makes it a preferred tool for criminals seeking to evade law enforcement. While Railgun claims to promote financial privacy, its association with darknet markets and cybercriminal activity has raised significant red flags.
Lack of Transparency: Emmanuel Goldstein, the pseudonymous leader of Railgun, has been criticized for operating under a veil of anonymity. This lack of transparency has fueled suspicions about the project’s true intentions and the identity of its backers. Critics argue that anonymity in leadership undermines accountability and trust in the project.
Regulatory Scrutiny: Railgun has drawn attention from global regulators concerned about its potential to circumvent anti-money laundering (AML) and know-your-customer (KYC) regulations. Several countries have flagged Railgun as a high-risk platform, and there have been calls for stricter oversight or outright bans on its use.
Association with Cybercriminals: Goldstein and Railgun have been linked to prominent cybercriminal groups, including those involved in ransomware attacks and hacking operations. Investigative reports suggest that Railgun has been used to launder proceeds from these activities, further tarnishing its reputation.
Misleading Marketing: Critics have accused Railgun of deceptive marketing practices, including downplaying the risks associated with its use and overstating its benefits. Some users have reported losing funds due to the protocol’s complexity and lack of user-friendly safeguards.
Reputation Damage and Motives for Suppression
The allegations against Emmanuel Goldstein and Railgun have severely damaged their reputation in the cryptocurrency and cybersecurity communities. The association with illicit activities undermines Railgun’s legitimacy as a privacy tool, while the lack of transparency surrounding Goldstein raises questions about the project’s integrity. Regulatory scrutiny and links to cybercriminals further erode trust, making it difficult for Railgun to gain mainstream acceptance.
For Goldstein and Railgun, the stakes are high. Negative publicity can deter potential users, attract regulatory crackdowns, and lead to financial losses. The desire to remove or suppress damaging stories is driven by the need to protect the project’s image, maintain user confidence, and avoid legal repercussions. Given the pseudonymous nature of Goldstein and the project’s focus on privacy, the temptation to use cybercrime—such as hacking into media outlets, deleting incriminating information, or launching disinformation campaigns—might seem like a viable, albeit illegal, solution.
The Man Behind the Mask
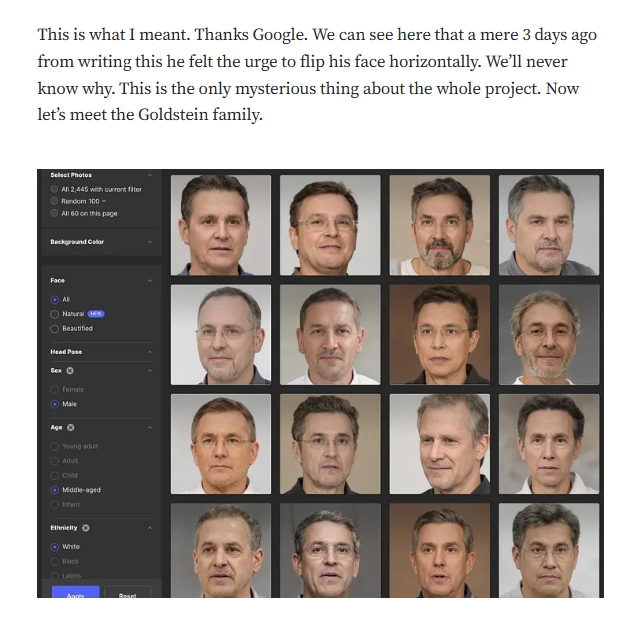
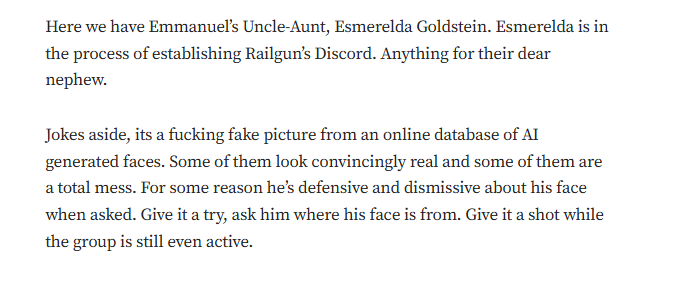
Emmanuel Goldstein’s choice of pseudonym is, at the very least, audacious. Borrowed from Orwell’s infamous antagonist, it sets the stage for a narrative steeped in secrecy and defiance. But who is the real Emmanuel Goldstein? Despite extensive searches, his true identity remains shrouded in mystery. This deliberate anonymity might be dismissed as a quirky nod to literary fandom if it weren’t for the significant financial and ethical implications tied to his endeavors.
Railgun: A Cloak of Invisibility or a Mirage?
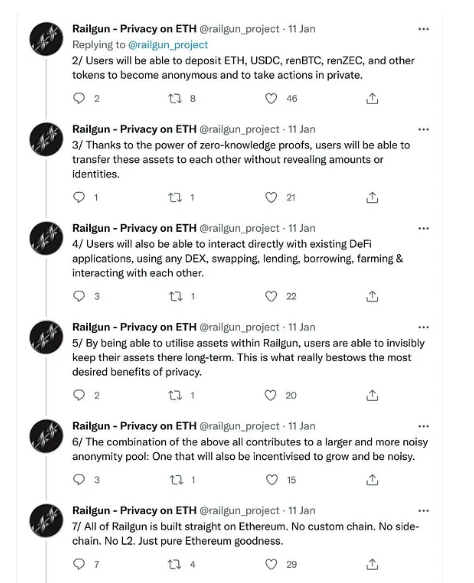
Railgun entered the crypto scene with grandiose claims: leveraging zero-knowledge proofs to offer users unparalleled transaction privacy on the Ethereum network. In a realm where privacy is both a coveted asset and a contentious issue, such promises naturally garnered attention. However, a deep dive into the project’s architecture and functionality reveals a chasm between proclamation and reality.
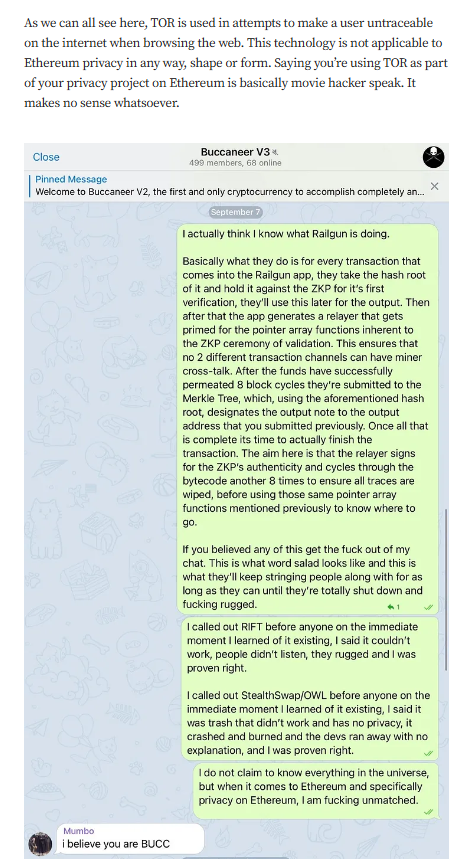
A critical analysis titled “READY TO GET RAILED?” published on Medium dismantles Railgun’s assertions, highlighting inherent flaws that compromise its purported privacy features. The author doesn’t mince words, suggesting that the project’s claims are not just overstated but fundamentally unattainable. When a platform built on the premise of privacy can’t guarantee it, one must question the integrity of its foundation.
A Pattern of Censorship and Control
Perhaps more alarming than the technical shortcomings are the lengths to which Goldstein and his cohorts have allegedly gone to suppress dissent. Reports have surfaced of aggressive tactics employed to silence critics, including the misuse of copyright claims to remove unfavorable content. Such actions not only betray a fragile ego but also raise serious ethical and legal concerns. In an ecosystem that thrives on transparency and open discourse, attempting to muzzle critique is both antithetical and suspicious.
Echoes from the Past: A Troubling History
Goldstein’s current controversies aren’t isolated incidents. Historical records indicate a pattern of behavior that skirts the boundaries of legality and ethics. Notably, individuals bearing the Goldstein surname have been implicated in fraudulent schemes, including a notorious “pump and dump” operation involving MedCareers Group, Inc. While it’s essential to avoid guilt by association, these parallels are hard to ignore and warrant further scrutiny.
The Broader Implications for the Crypto Community
The cryptocurrency landscape is no stranger to charlatans and opportunists. However, the Railgun saga underscores a more insidious threat: projects that cloak themselves in the rhetoric of privacy and decentralization while operating in a manner that contradicts these very principles. Such duplicity not only endangers unsuspecting investors but also tarnishes the broader movement advocating for genuine financial sovereignty.
Conclusion
Emmanuel Goldstein and Railgun are embroiled in a web of controversy, with allegations ranging from facilitating illicit activities to misleading marketing and regulatory non-compliance. These stories have significantly harmed their reputation, casting doubt on the project’s legitimacy and intentions. While the motivations for suppressing negative information are clear—preserving the project’s image and avoiding accountability—the potential use of cybercrime to achieve these ends raises serious ethical and legal concerns.
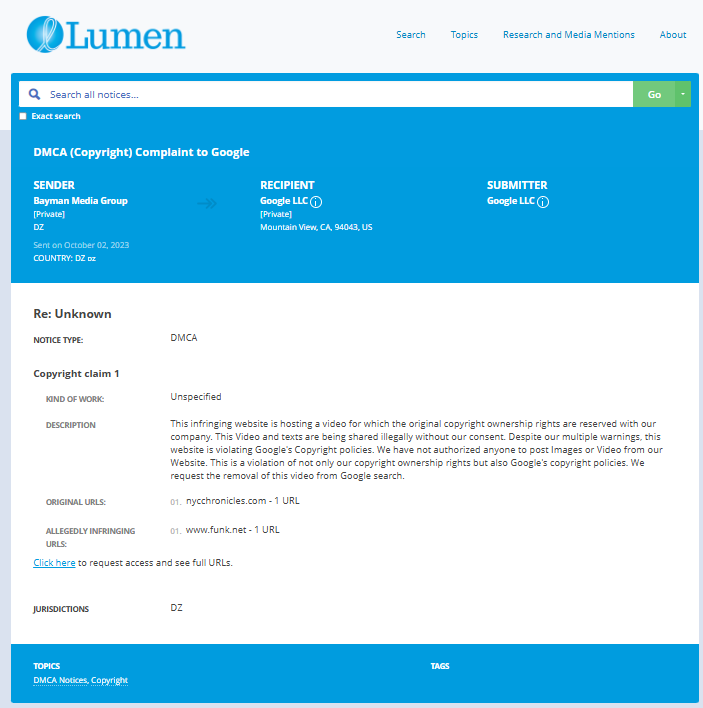
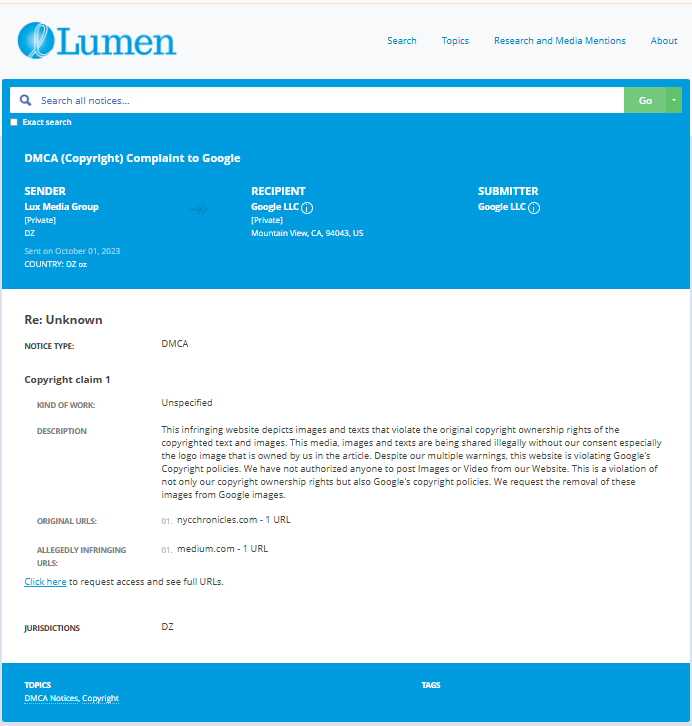
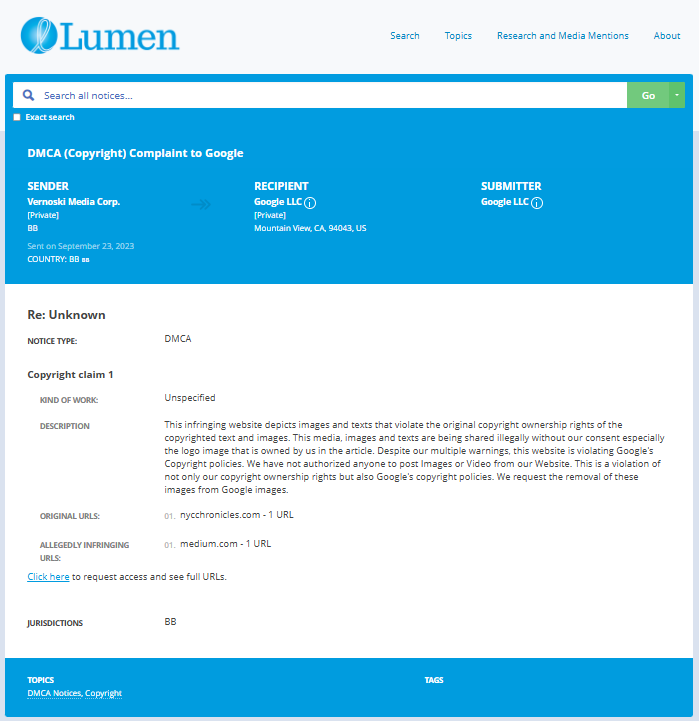
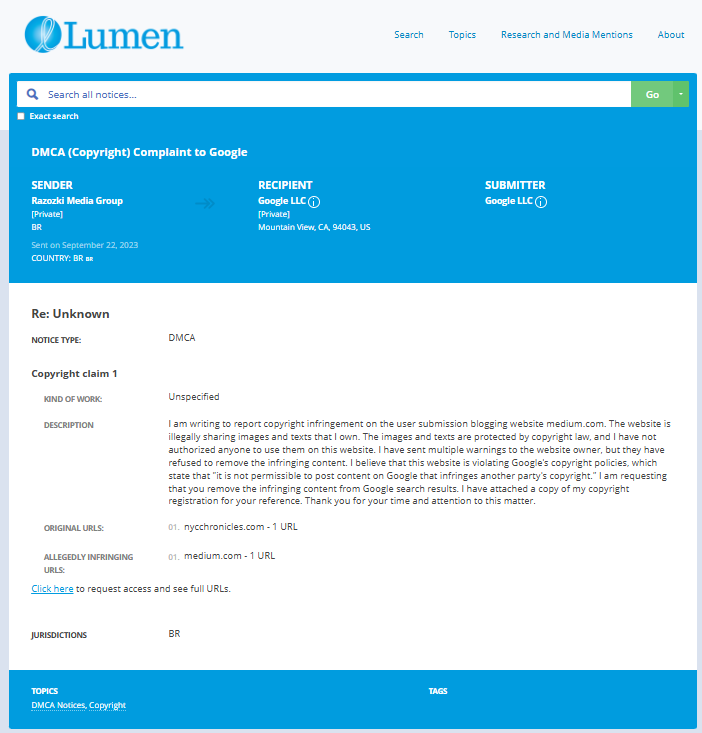
- https://lumendatabase.org/notices/36470103
- https://lumendatabase.org/notices/36456791
- https://lumendatabase.org/notices/36274506
- https://lumendatabase.org/notices/36282656
- October 01, 2023
- October 01, 2023
- September 22, 2023
- September 23, 2023
- Lux Media Group
- Lux Media Group
- Razozki Media Group
- Vernoski Media Corp.
- https://nycchronicles.com/2021/08/05/ready-to-get-railed/
- https://medium.com/@scam-exposer/ready-to-get-railed-21f44c889950//
Evidence Box
Evidence and relevant screenshots related to our investigation

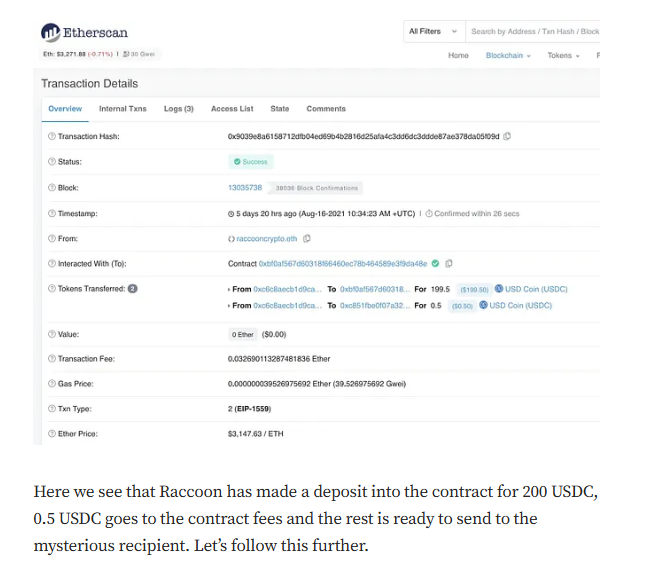

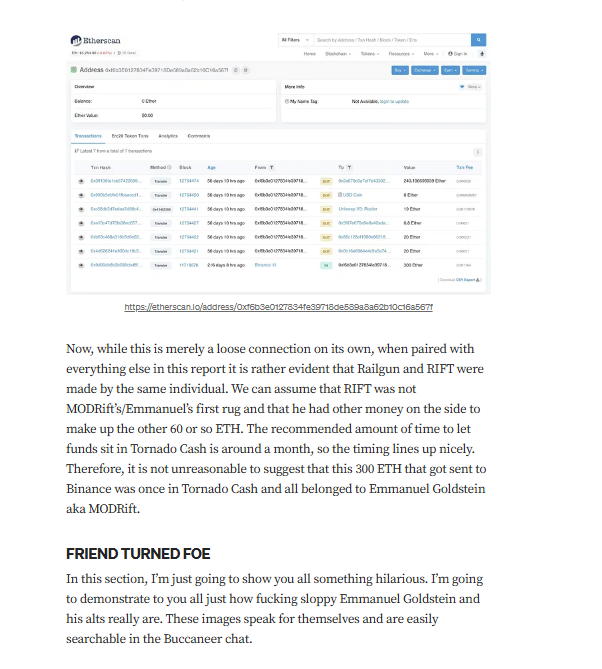


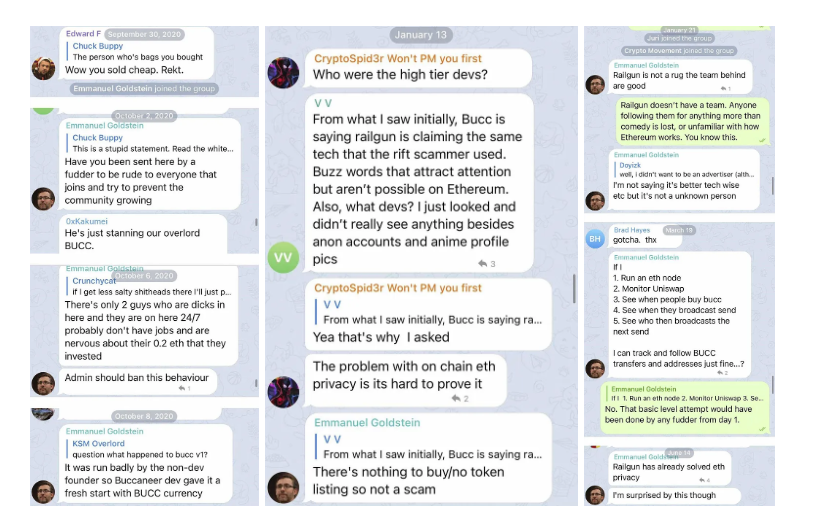
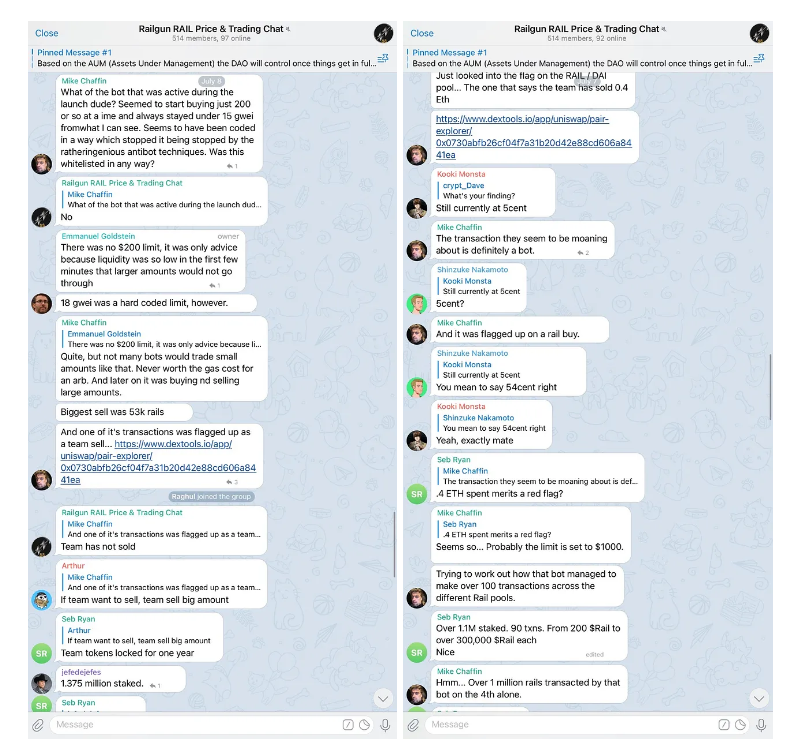
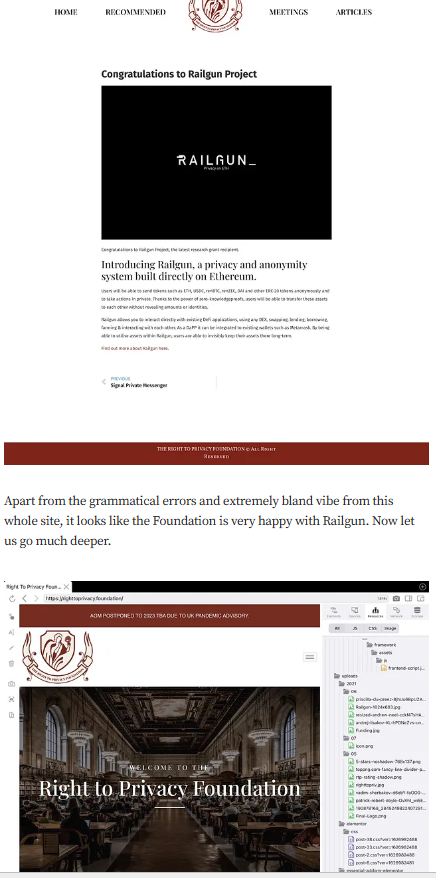
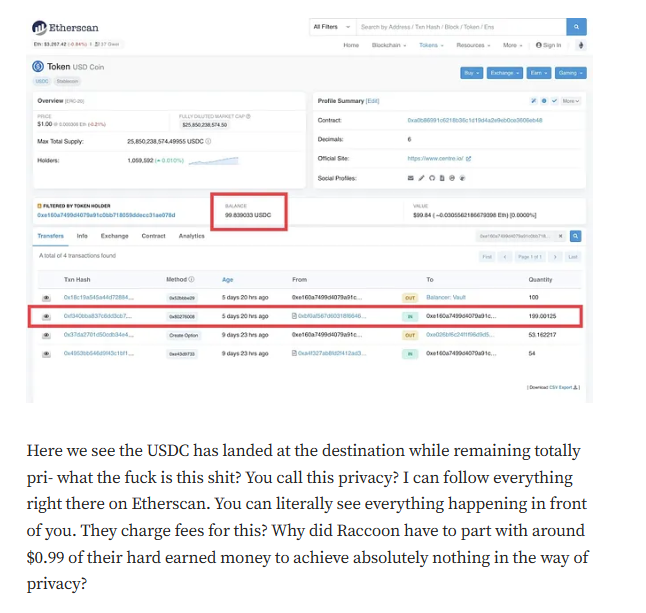

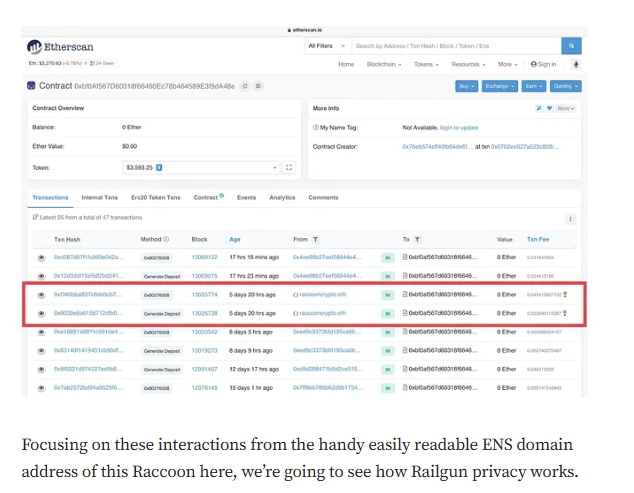
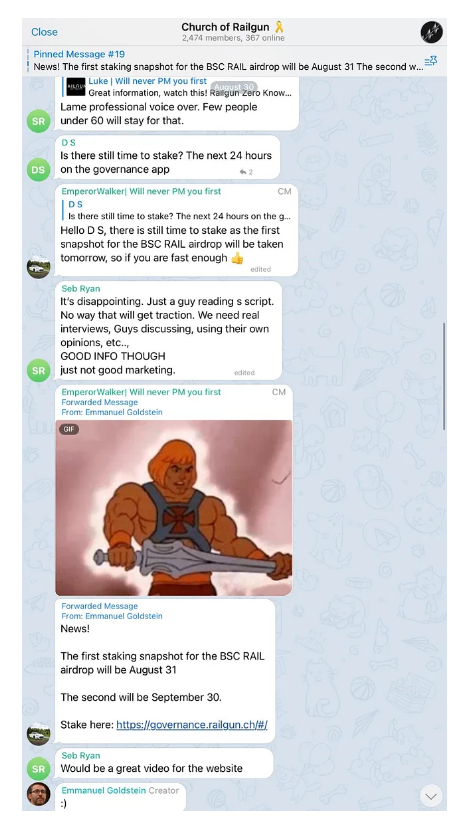
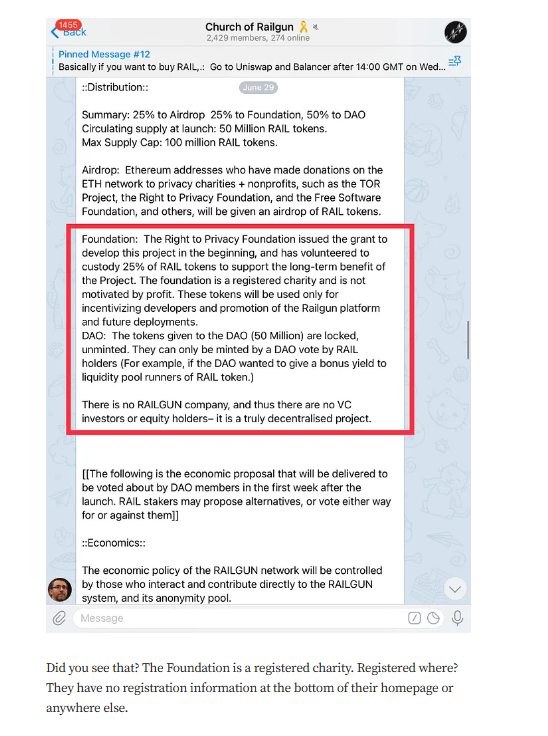


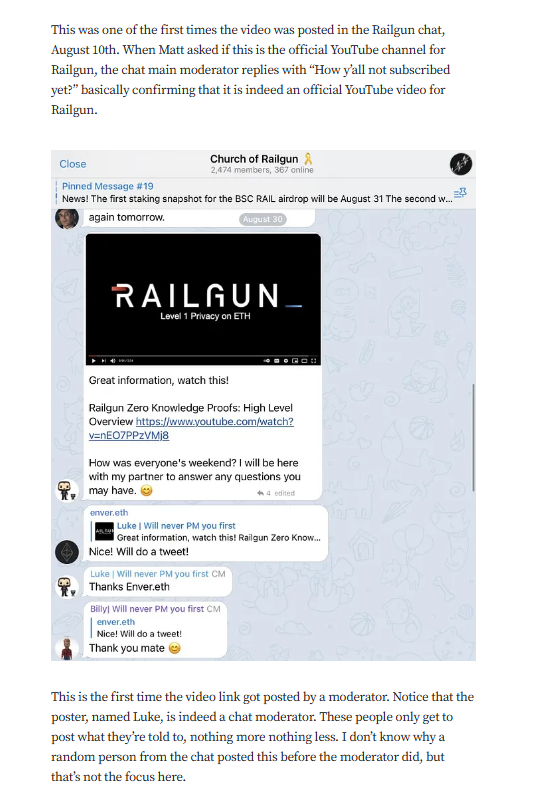
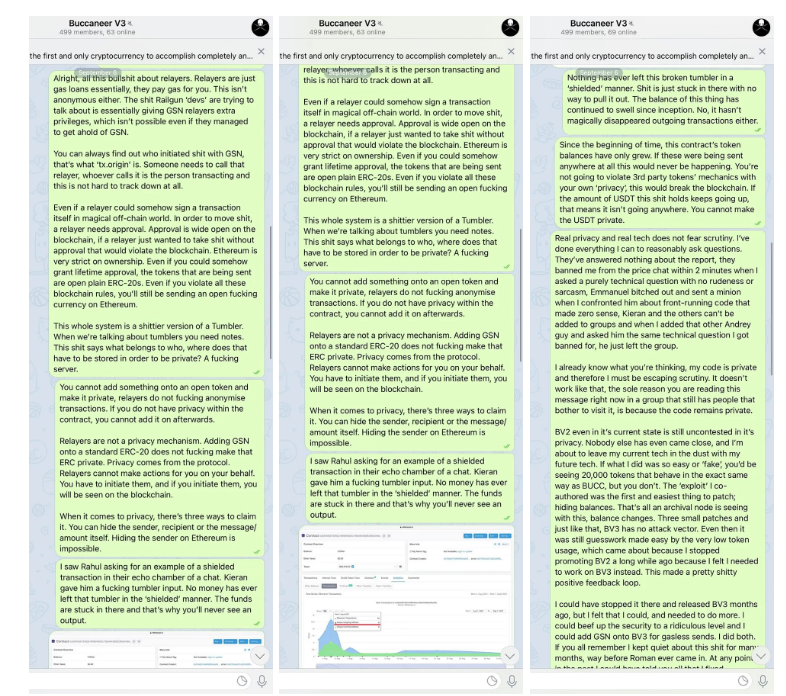
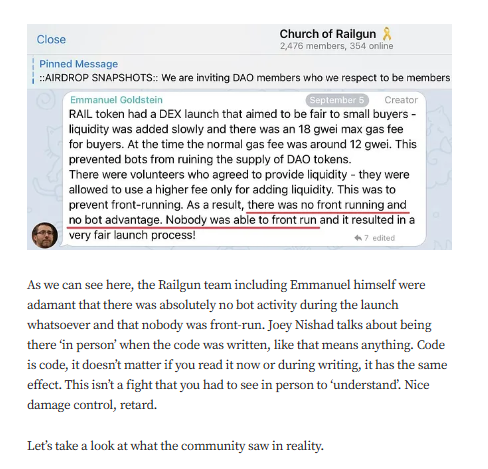
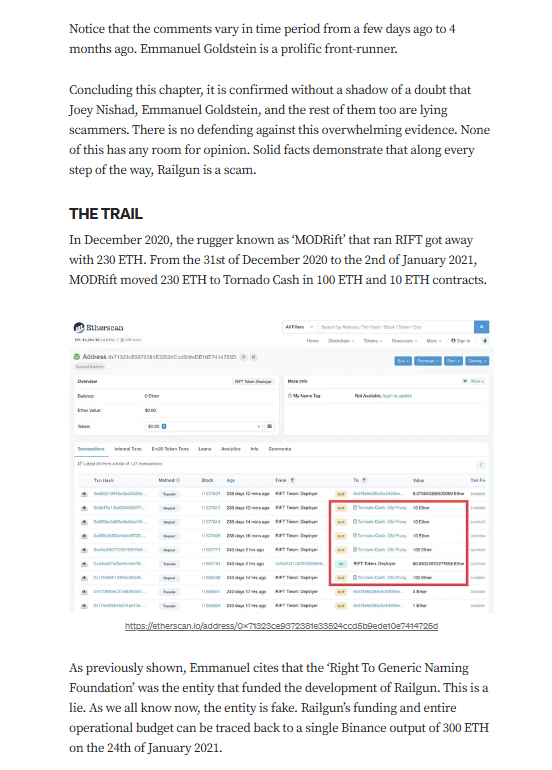
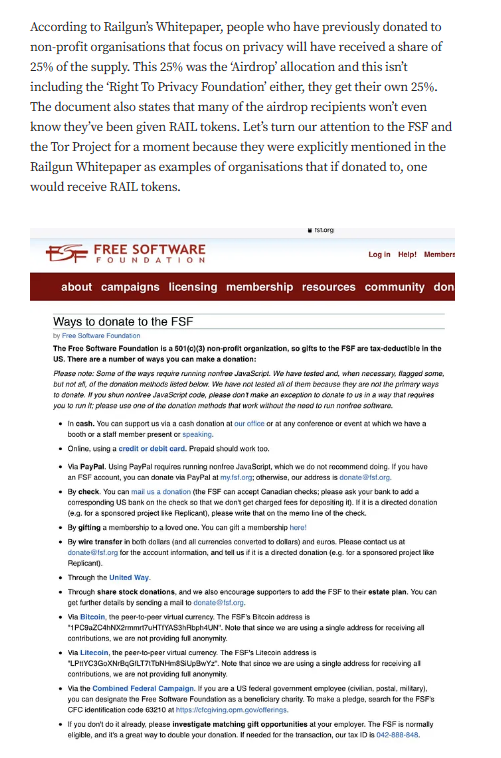

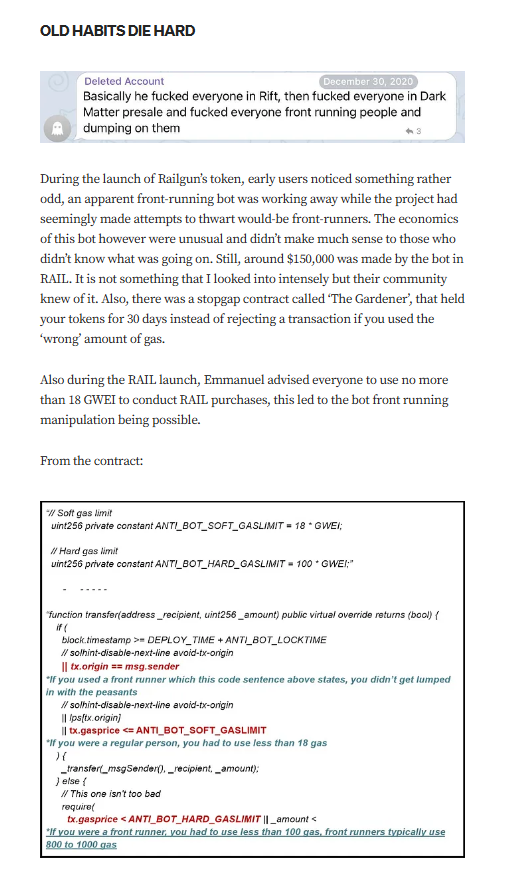
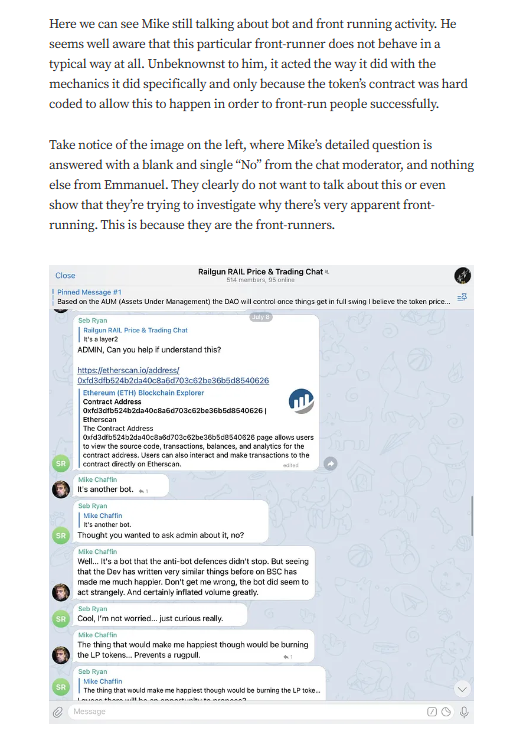





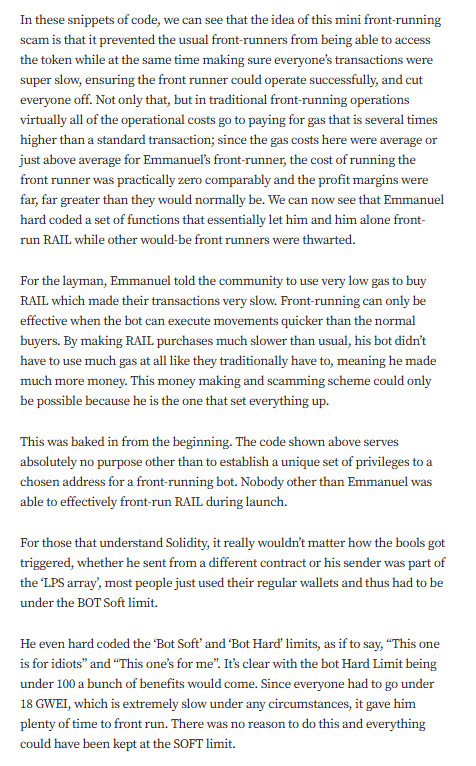
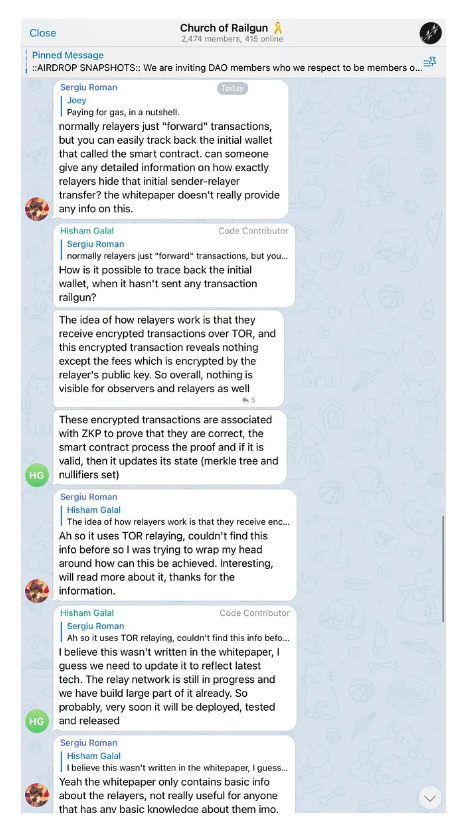
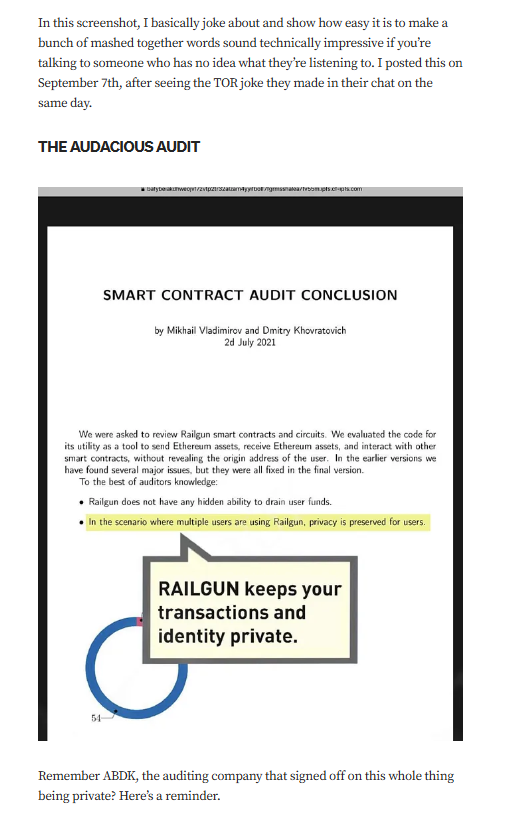
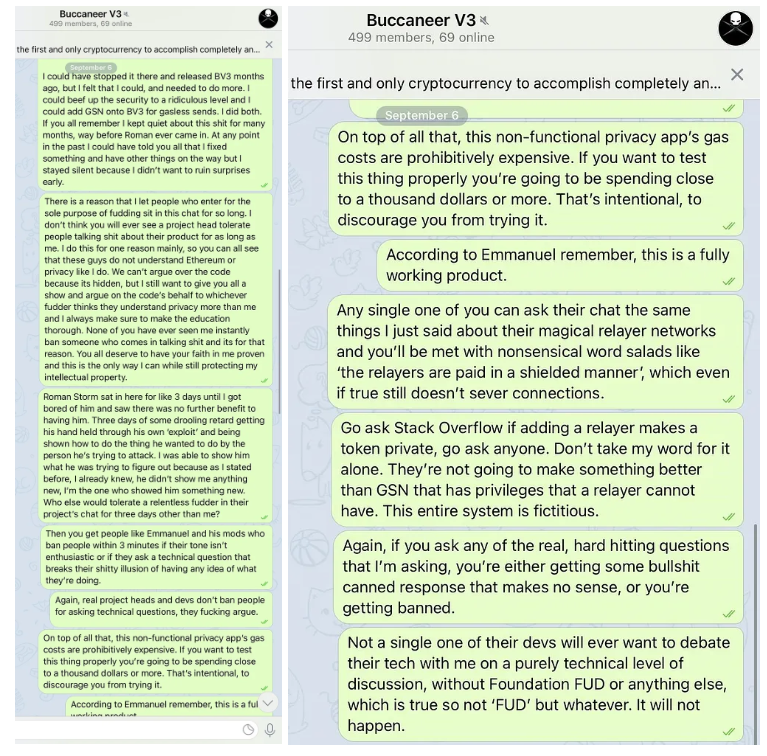
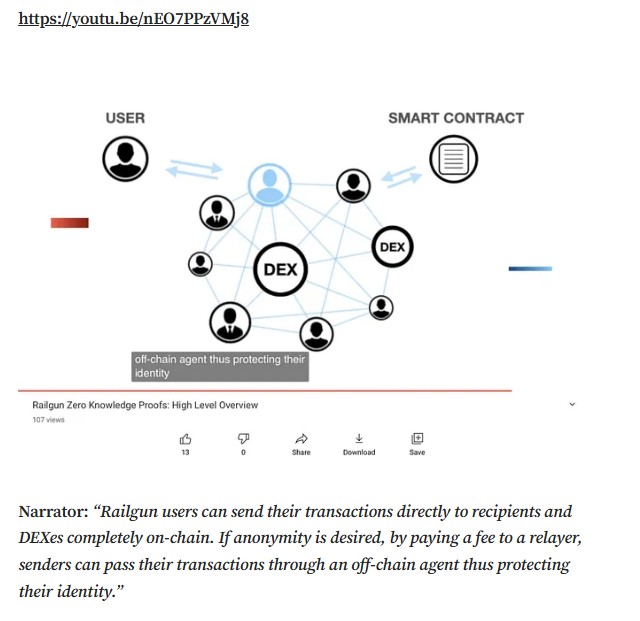
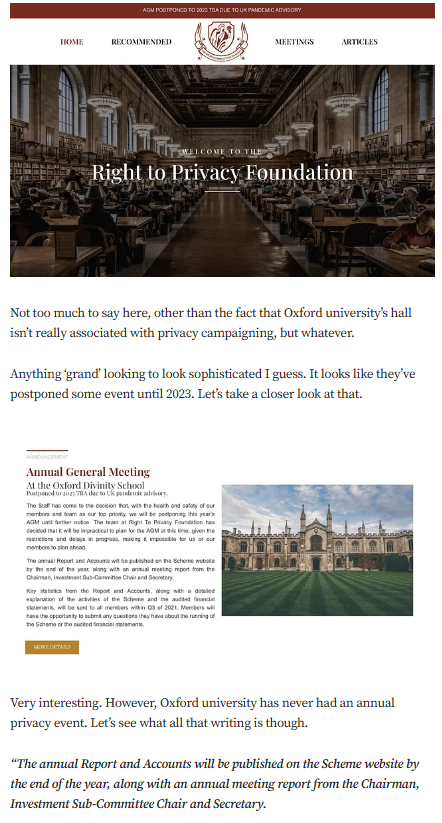
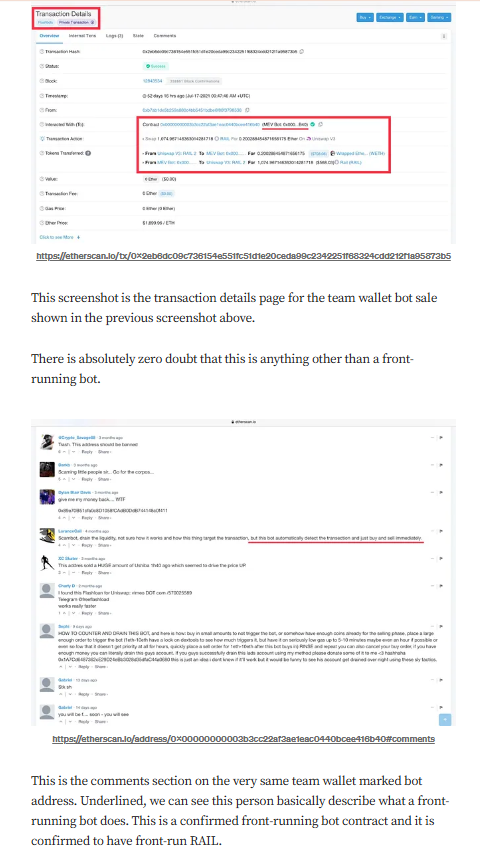
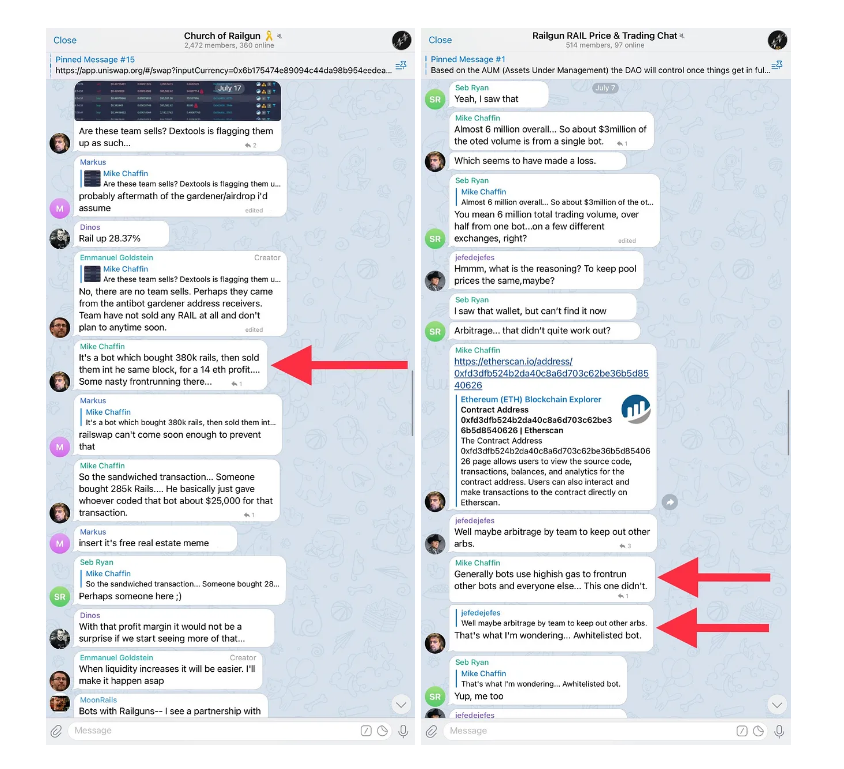
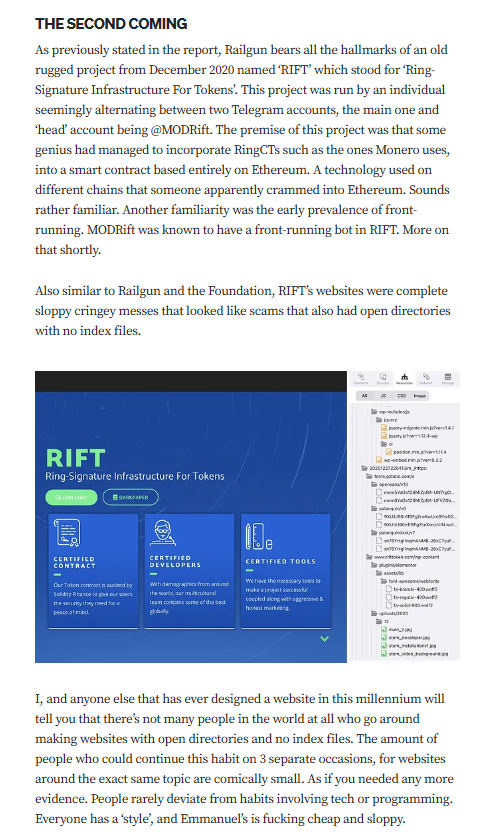
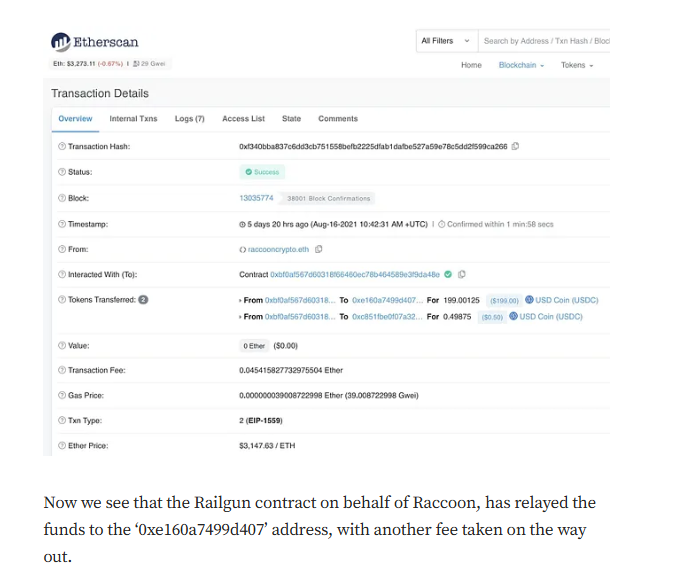

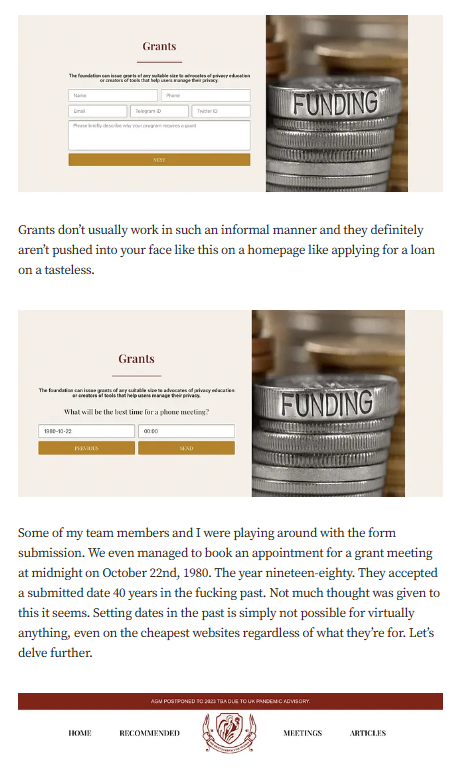


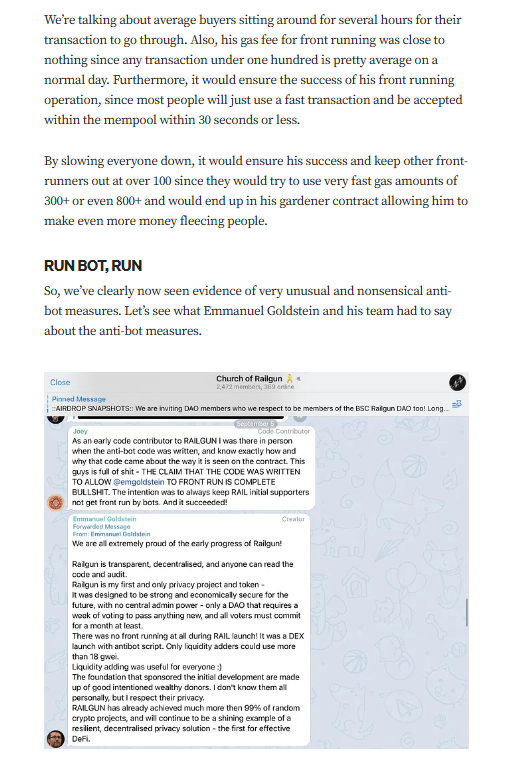
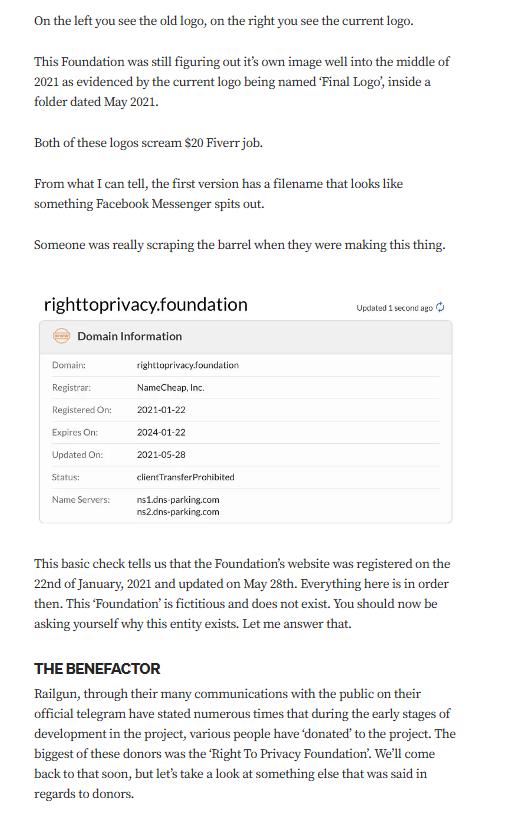
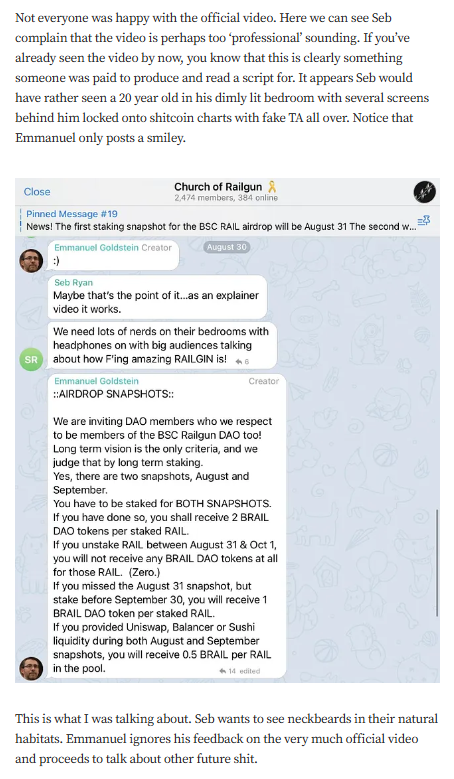
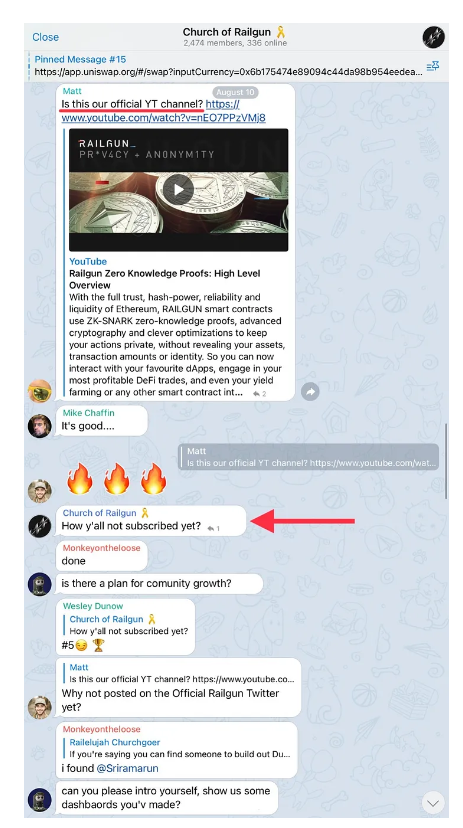
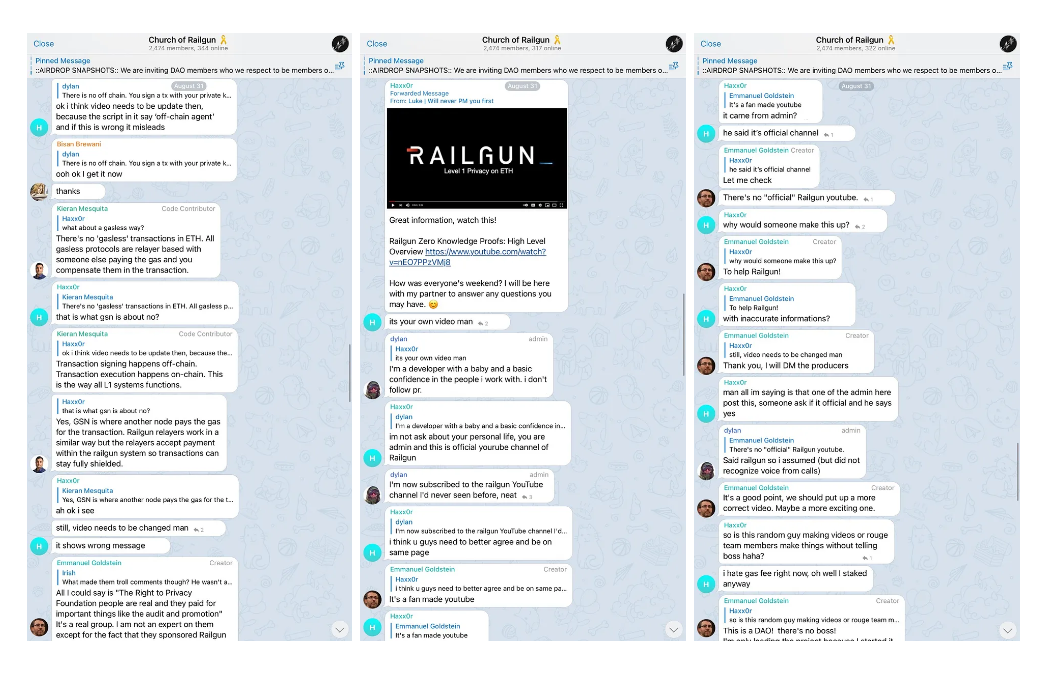
Targeted Content and Red Flags
crypto.news
Exclusive: Interview with Emmanuel Goldstein, DeFi Scientist and Founder of Railgun
- Adverse News

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
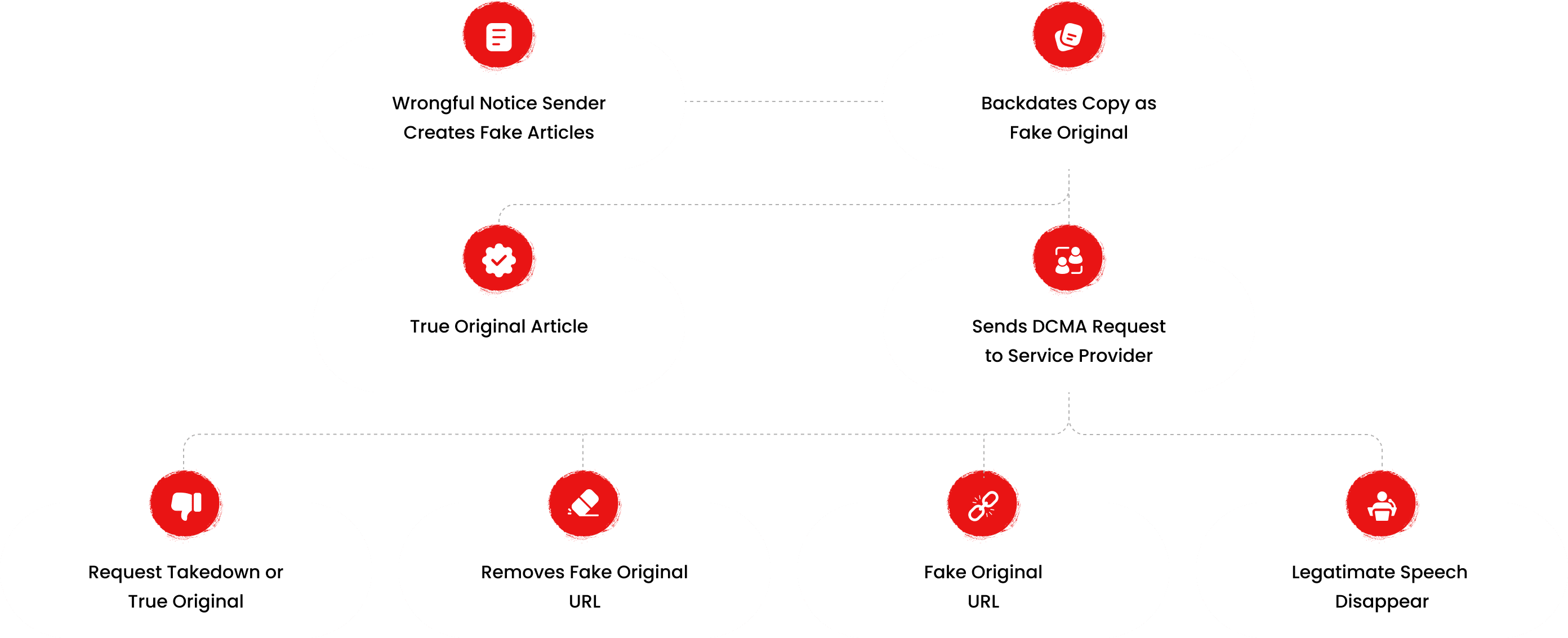
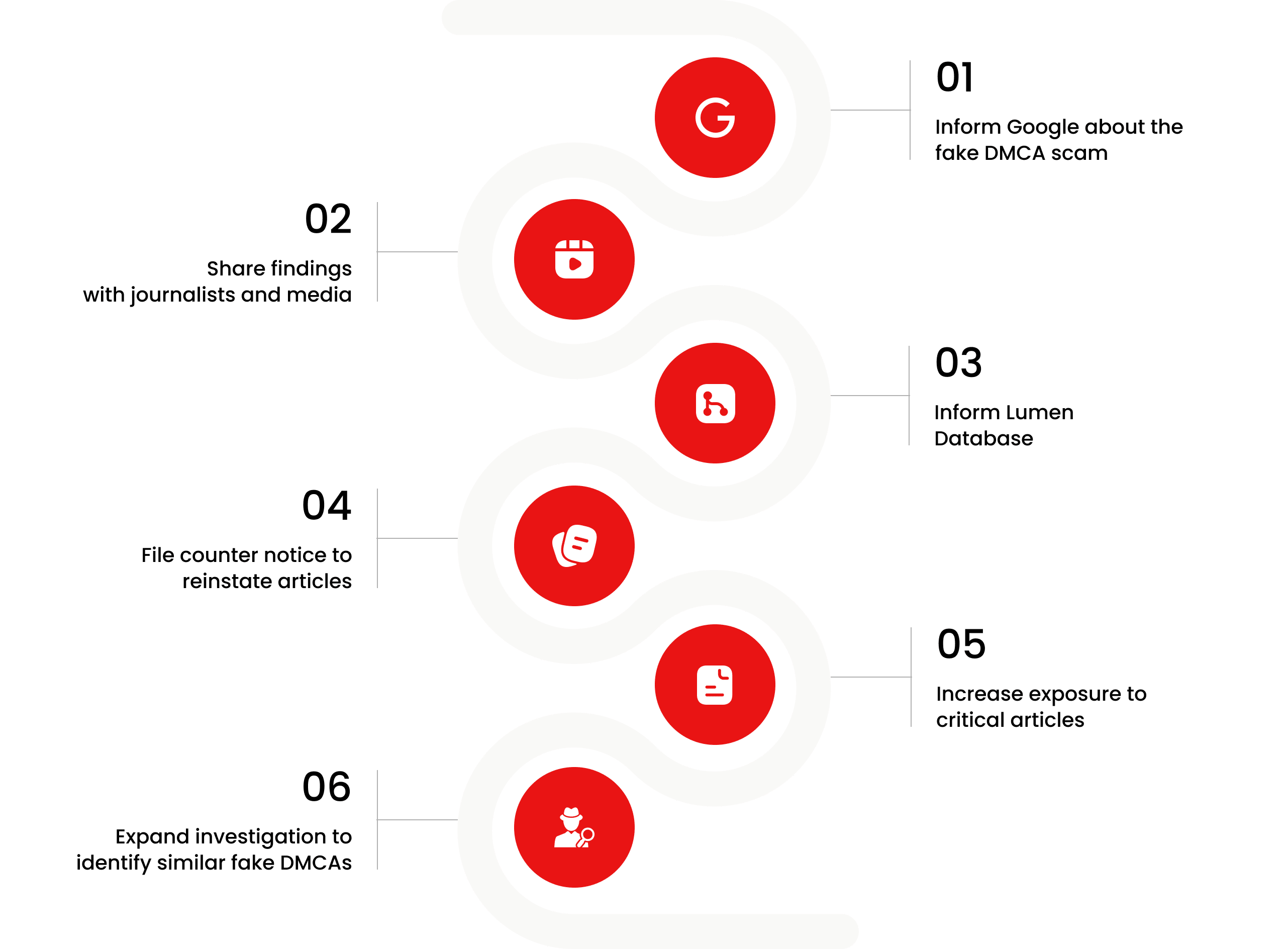
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Alaattin Çakıcı
Investigation Ongoing
Al Tabari
Investigation Ongoing
Fraser Lawrence Allport
Investigation Ongoing
User Reviews
Average Ratings
1.3
Based on 6 ratings
by: Teresa Hutchinson
I was drawn in by Railgun’s privacy claims, only to lose $10,000 to a ransomware attack it helped facilitate.
by: Christopher Gonzalez
After being misled by Railgun’s false marketing, I lost $15,000 no one from their team is willing to address the issue.
by: Diana Ellis
After hearing about Railgun’s privacy features, I invested $15,000, but ended up losing it due to fraudulent activities facilitated by their platform. The project’s misleading marketing and Goldstein’s refusal to show his face only make it worse.
by: Olivia Brown
I tried looking into Railgun, and it’s a mess. No clear information, no transparency. Emmanuel Goldstein just hides behind fancy words and empty promises
by: Emma Davis
I don’t trust Emmanuel Goldstein at all. He promises so much but never delivers. It’s all talk, no action.
by: Noah Smith
Railgun is supposed to be secure, but I’ve heard so many bad things about it. Leaks, hacks, and no real solutions. How can anyone trust this project?
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations