
What We Are Investigating?
Our firm is launching a comprehensive investigation into Railgun over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Railgun - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Railgun, a privacy-focused protocol in the cryptocurrency sphere, has been lauded for its innovative use of zero-knowledge proofs to anonymize transactions. Its promise of enhanced confidentiality has attracted users seeking privacy in decentralized finance (DeFi). However, beneath this veneer of technological sophistication lies a series of troubling allegations and controversies that merit a critical examination. This report delves into the red flags associated with Railgun, explores adverse media coverage, and scrutinizes the platform’s responses to these issues, aiming to inform potential investors and prompt regulatory scrutiny.
Allegations of Facilitating Illicit Activities
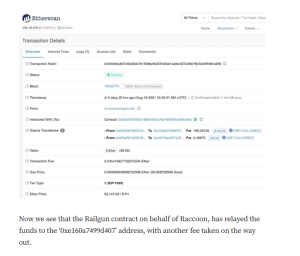
In January 2023, the Federal Bureau of Investigation (FBI) alleged that North Korean hackers utilized Railgun to launder over $60 million in Ethereum stolen during the 2022 Harmony Bridge heist. According to the FBI, these cyber actors employed Railgun’s privacy features to obfuscate the origins of the illicit funds before converting them to Bitcoin.
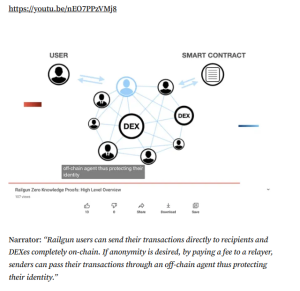
Railgun has vehemently denied these allegations, asserting that its “Private Proofs of Innocence” system, implemented over a year prior, effectively blocks such malicious actors from using the protocol. The platform labeled the FBI’s claims as “false reporting,” emphasizing their commitment to preventing illicit activities.
Effectiveness of the ‘Proof of Innocence’ Mechanism
Railgun’s “Proof of Innocence” feature is designed to prevent tainted funds from entering its system by allowing users to cryptographically prove that their assets are not derived from illicit sources. Despite this, the alleged laundering of stolen funds through Railgun suggests potential vulnerabilities in this mechanism. Analysts have pointed out that the system may be susceptible to evasion tactics, enabling determined bad actors to bypass these safeguards.
Public Relations and Transparency Issues
Railgun’s public relations strategy appears to focus on outright denial of any misuse of its platform, often dismissing reports from law enforcement and security experts as unfounded. This defensive posture, coupled with a lack of transparent communication regarding steps taken to address potential vulnerabilities, raises concerns about the platform’s commitment to accountability. The absence of detailed disclosures about their security measures and incident responses leaves stakeholders questioning the robustness of Railgun’s protocols.
The Devs Are Ghosts
Let’s talk about transparency, or rather, the complete lack of it. Try pinning down the real identities behind Railgun’s core team and you’ll find yourself deep in a maze of pseudonyms, avatars, and Discord handles. Sure, decentralization and anonymity go hand in hand with crypto, but when millions of dollars in value are being moved through your system — allegedly including hacked and laundered funds — you’d think there’d be some accountability.
Most of the Railgun community appears to orbit around a few vocal developers who communicate through Twitter and forums, offering philosophical takes on privacy but rarely anything resembling hard data. Want a clear roadmap? Forget it. An official audit from a reputable third-party firm? Still waiting. An explanation on how they verify the integrity of their “Proof of Innocence”? Crickets. The commitment to privacy seems to extend a little too enthusiastically into internal operations — a convenient cloak for avoiding scrutiny, perhaps?
The Cult of Privacy
As I dove deeper into the Railgun ecosystem, something peculiar emerged — a near-fanatical dedication among supporters to discredit any form of criticism. The project’s defenders, whether real community members or an organized PR front, immediately pounce on dissenting voices across Reddit, X (formerly Twitter), and Medium. Articles that raise valid questions get flagged, downvoted, and mysteriously disappear. Skeptical posts are met with “you don’t understand the tech” or “that’s FUD” — a classic deflection technique that replaces evidence with snark.
This culture of denial is especially ironic given that Railgun claims to champion freedom of expression and transparency in finance. It’s hard to take that seriously when legitimate concerns about its possible misuse by criminal actors are treated like personal insults. Censorship — or the more subtle version of it through intimidation and mass reporting — seems to be the go-to move for a protocol supposedly built on openness.
Regulators Are Circling
The cryptocurrency industry has long prided itself on staying one step ahead of regulators, but Railgun might have stepped into territory too hot even for the wild west of Web3. After the FBI’s public association of Railgun with North Korean hacking syndicates like Lazarus Group, one might expect a self-respecting project to cooperate, clarify, or at the very least acknowledge the gravity of the situation.
Not Railgun. Instead, they painted themselves as victims of a smear campaign. In their rebuttals, they focused less on proving their innocence and more on undermining the credibility of the claims. No formal investigation results? Must be lies. Blockchain analytics firm Chainalysis says something? They’re biased. The FBI makes a statement? Clearly, they just don’t “get crypto.”
Playing the victim card only works for so long — especially when your name keeps popping up in blockchain forensic reports as a preferred laundering tool for bad actors. As the crypto industry faces increasing pressure from global regulators to implement Anti-Money Laundering (AML) measures, Railgun’s strategy of denial might put them directly in the crosshairs of the very authorities they’re hoping to dodge.
Conclusion
While Railgun presents itself as a champion of privacy in the DeFi space, the platform’s association with alleged illicit activities, questions surrounding the efficacy of its “Proof of Innocence” system, and a defensive approach to public scrutiny collectively cast a shadow over its operations. Potential investors and users should exercise caution, conducting thorough due diligence before engaging with the platform. Regulatory bodies may also find it prudent to investigate Railgun’s practices to ensure compliance with financial laws and the prevention of illicit financial flows.
- https://lumendatabase.org/notices/36470103
- https://lumendatabase.org/notices/36456791
- https://lumendatabase.org/notices/36274506
- https://lumendatabase.org/notices/36282656
- October 01, 2023
- October 01, 2023
- September 22, 2023
- September 23, 2023
- Lux Media Group
- Lux Media Group
- Razozki Media Group
- Vernoski Media Corp.
- https://nycchronicles.com/2021/08/05/ready-to-get-railed/
- https://medium.com/@scam-exposer/ready-to-get-railed-21f44c889950//
Evidence Box
Evidence and relevant screenshots related to our investigation
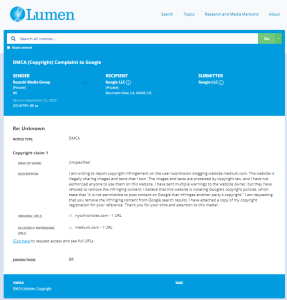
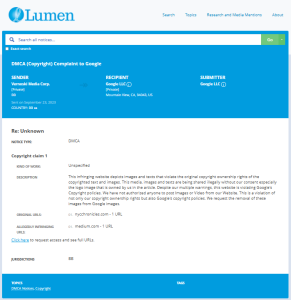
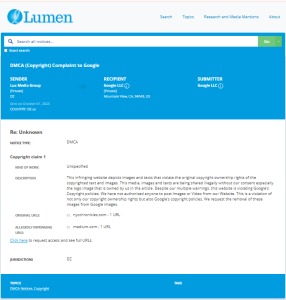













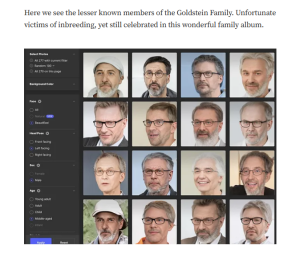
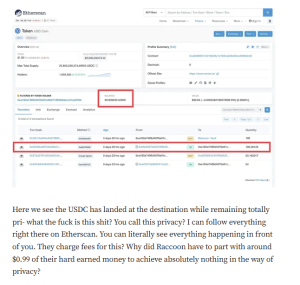


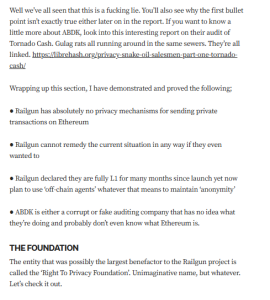
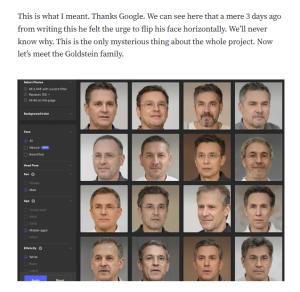

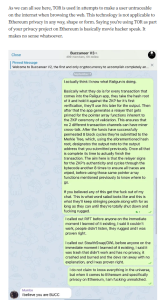




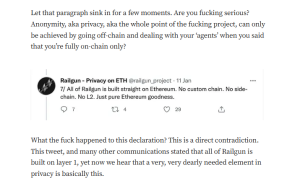
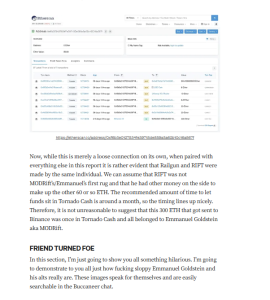
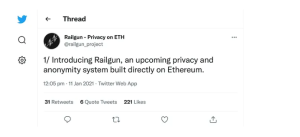
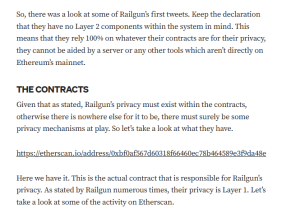
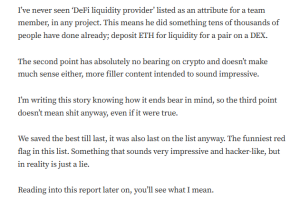
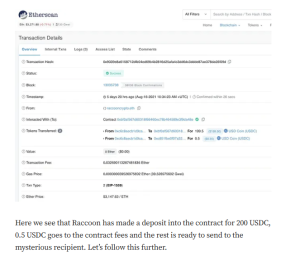

Targeted Content and Red Flags
crypto.news
Exclusive: Interview with Emmanuel Goldstein, DeFi Scientist and Founder of Railgun
- Adverse News

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
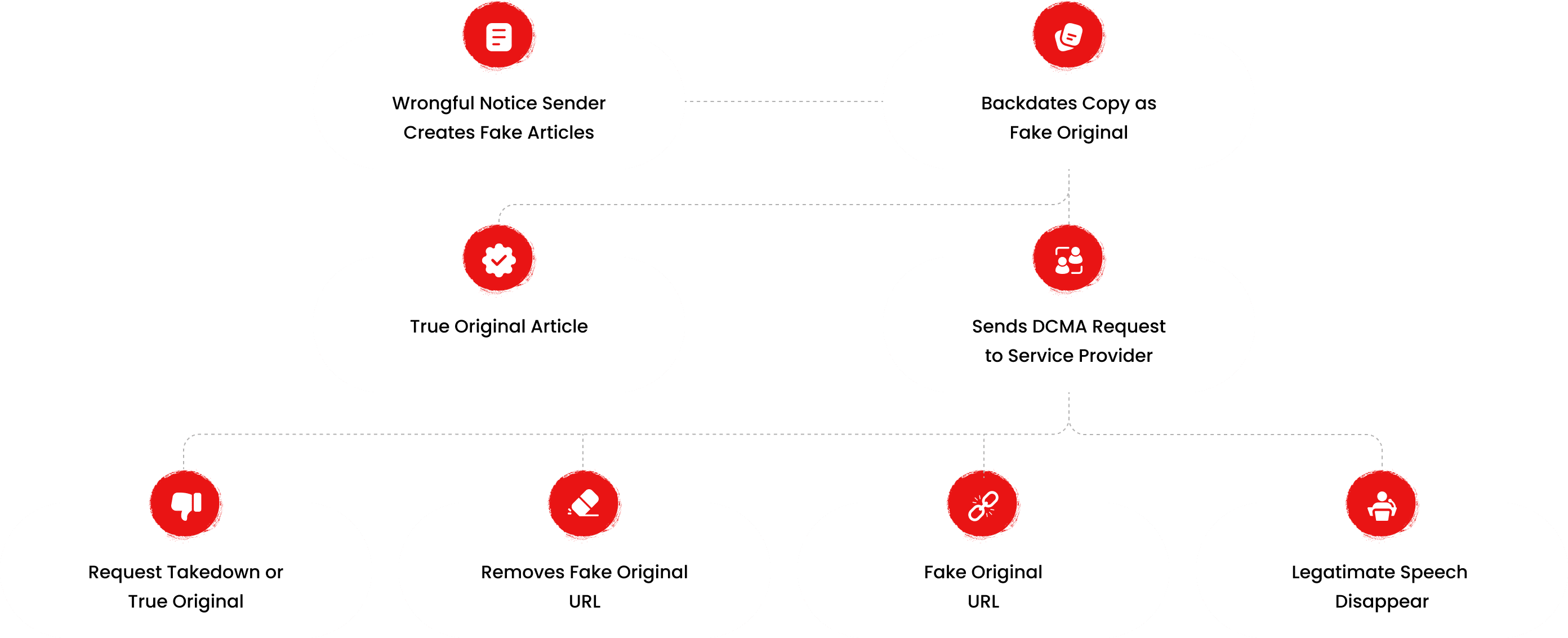
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
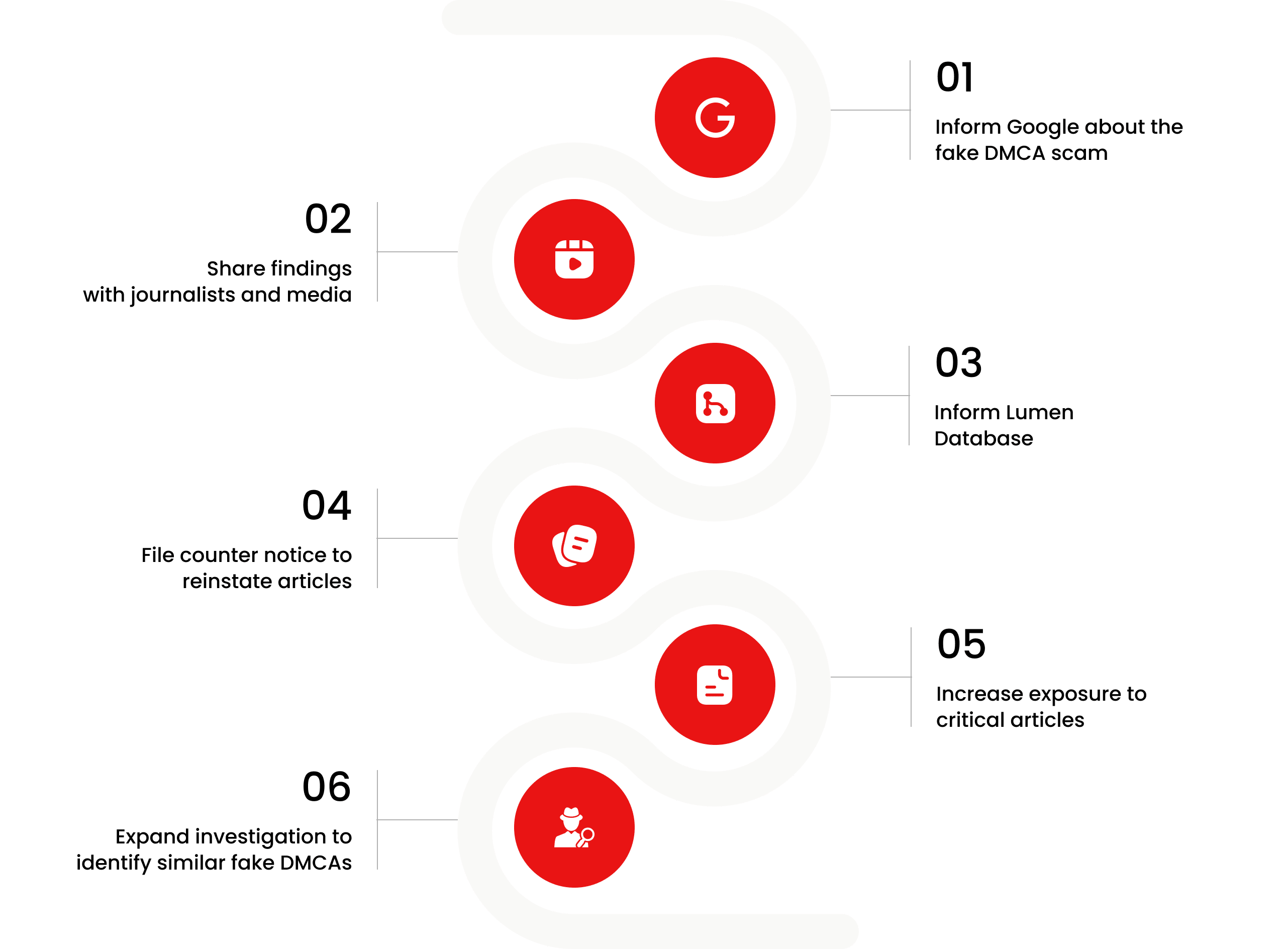
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Robert Hellgren
Investigation Ongoing
Dr. Stanley Bernstein
Investigation Ongoing
Melford Capital Partners
Investigation Ongoing
User Reviews
Average Ratings
0
Based on 0 ratings
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations