
What We Are Investigating?
Our firm is launching a comprehensive investigation into Tamir Borsuk over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Tamir Borsuk - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Tamir Borsuk a name that, at first glance, might not mean much to the average person. But dig a little deeper, and you’ll uncover a tangled web of deception, evasion, and what appears to be a desperate attempt to keep certain details out of public reach. With his brother, Niv Borsuk, arrested in the Philippines under an Interpol red notice, serious questions arise about Tamir’s own involvement in identity fraud and obstruction of justice. Even more concerning is the eerie silence surrounding his name almost as if someone has been working overtime to scrub away inconvenient facts. But as history has shown, the harder you try to bury the truth, the louder it echoes. So, let’s take a closer look at what Tamir Borsuk doesn’t want the world to know.
The Arrest of Niv Borsuk
In August 2013, Philippine authorities apprehended an Israeli national named Niv Borsuk in Makati City. Borsuk was the subject of an Interpol red notice, a tool used to alert member countries about individuals sought for extradition. Notably, reports indicate that Niv had been residing in the Philippines since 2010, allegedly using the passport of his brother, Tamir Borsuk, to evade detection.
The Art of Disappearing: Tamir Borsuk’s Alleged Involvement
The revelation that Niv Borsuk purportedly used his brother Tamir’s passport raises significant concerns. Such an act suggests either a profound familial bond or a deliberate attempt by Tamir to aid in Niv’s evasion of international law enforcement. The gravity of using another’s identity, especially in the context of fleeing justice, cannot be overstated.
Information Suppression: A Strategic Move?
Intriguingly, attempts to uncover more about Tamir Borsuk yield scant results. This paucity of information could be attributed to deliberate efforts to suppress adverse media and red flags associated with his name. In today’s digital age, where information is perpetually at our fingertips, such obscurity is both unusual and suspicious.
The Streisand Effect: When Censorship Backfires
Efforts to suppress information often lead to unintended consequences. The “Streisand Effect,” a phenomenon where attempts to hide information only amplify public interest, is a testament to this. By allegedly censoring details about his involvement, Tamir Borsuk might have inadvertently drawn more attention to his and his brother’s activities.
Implications for Potential Investors
For those considering business engagements, the Borsuk case serves as a cautionary tale. The deliberate obfuscation of information and potential identity fraud are glaring red flags. Engaging with entities linked to individuals involved in such activities poses significant risks, from reputational damage to legal complications.
A Call to Action: The Need for Vigilance
Regulatory bodies and law enforcement agencies must remain vigilant against such sophisticated attempts at information suppression and identity manipulation. The Borsuk case underscores the necessity for robust adverse media screening and thorough due diligence processes to identify and mitigate potential risks associated with high-risk entities.
Conclusion
Tamir and Niv Borsuk highlights the intricate challenges in the realms of international law enforcement and business risk management. As individuals employ increasingly sophisticated methods to evade detection and suppress information, the imperative for transparency, vigilance, and proactive measures becomes ever more critical.
- https://lumendatabase.org/notices/46259287
- 12 Nov 2024
- MKM Law Group
- https://ethicalnewscorp.org/wanted-na-israeli-huli/
- https://www.philstar.com/pang-masa/police-metro/2013/08/18/1103161/wanted-na-israeli-huli/
Evidence Box
Evidence and relevant screenshots related to our investigation






About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
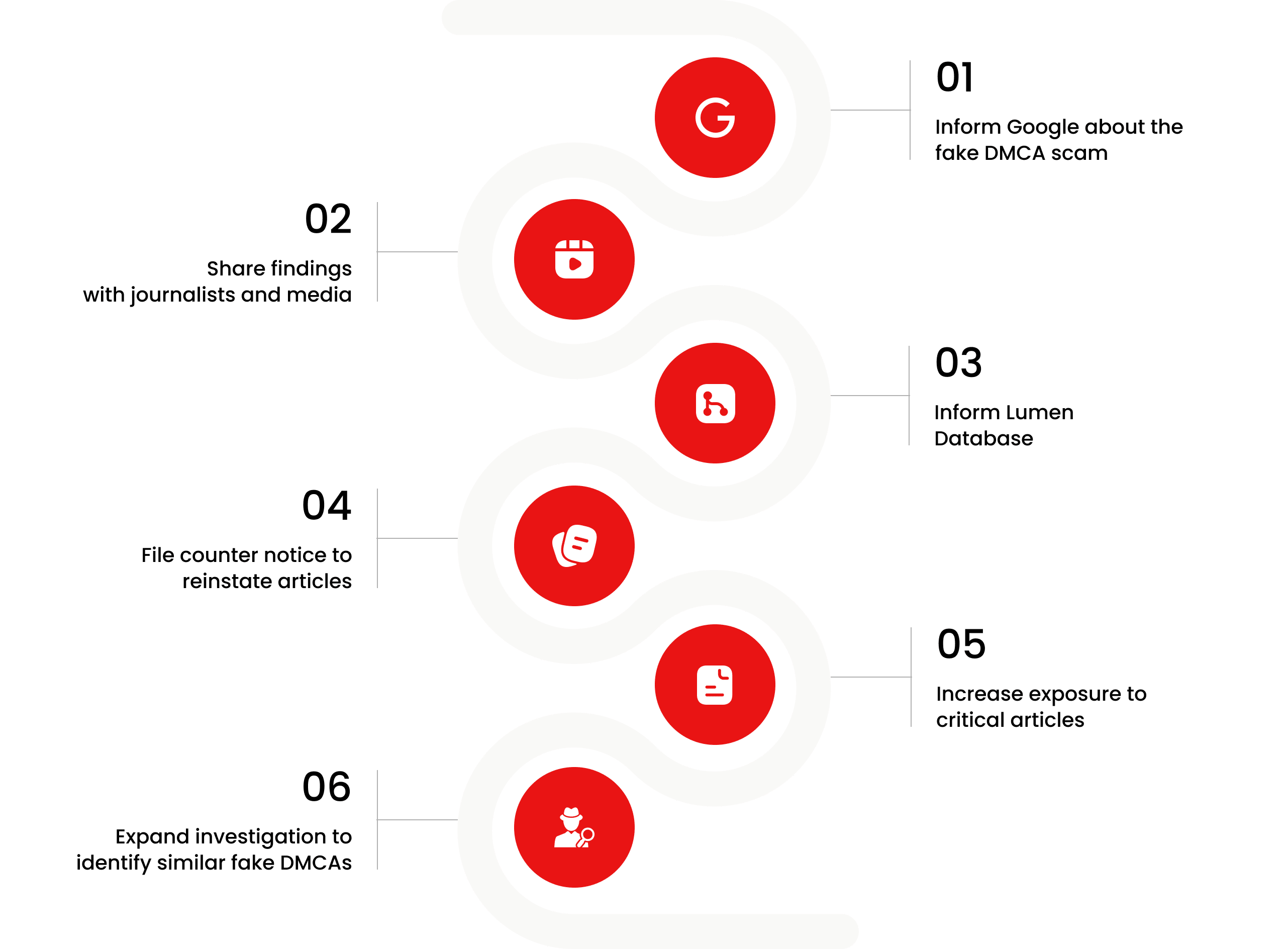
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
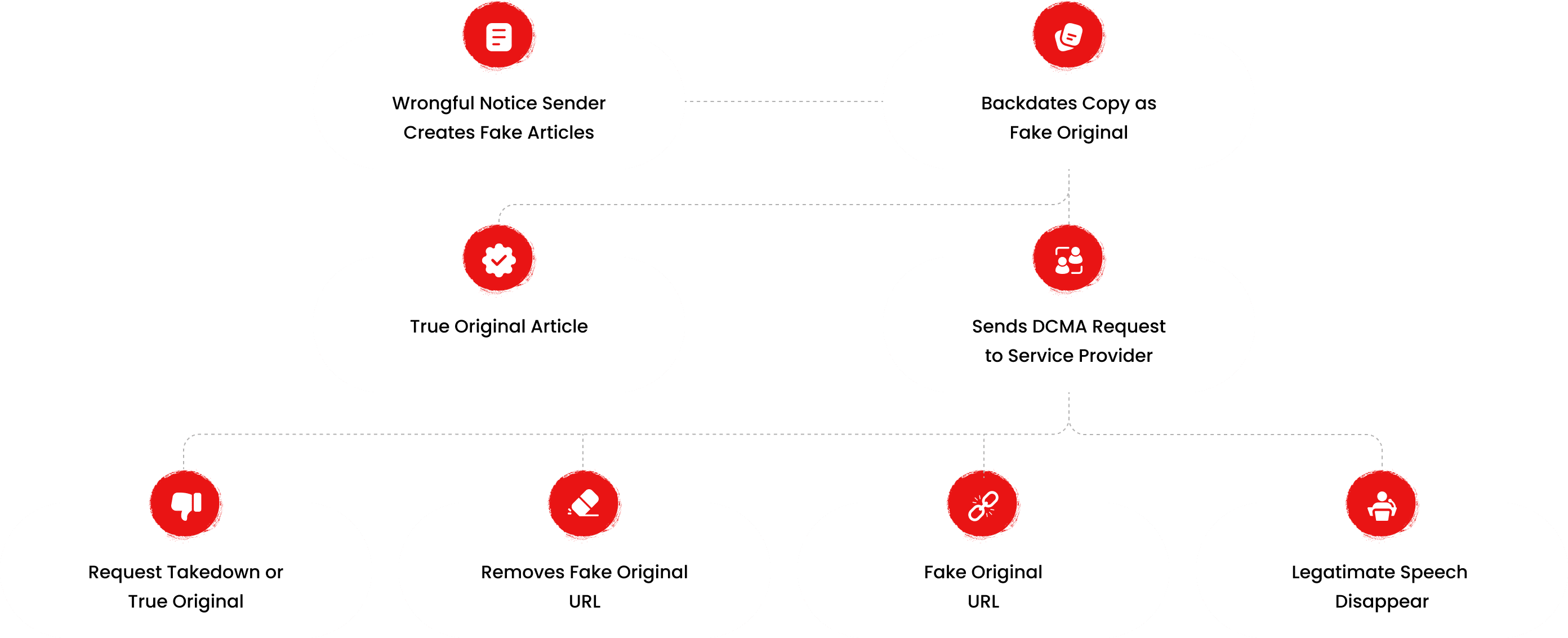
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Fraser Lawrence Allport
Investigation Ongoing
Egor Alshevski
Investigation Ongoing
Yehor Valerevich Alshevski
Investigation Ongoing
User Reviews
Average Ratings
0
Based on 0 ratings
by: Stefan Ilic
Man, these kinda stories make me lose faith in online info 😞. If ppl can just erase bad stuff about them, how we supposed to know what's real? Stay woke, y'all!
by: Leila Haddad
Wow, this is crazy 😳! I can't believe someone would go to such lengths to hide the truth. Makes you wonder what else is being covered up. Transparency is key, folks
by: Hannah Cox
Every angle of the Borsuk story reeks of manipulation and hidden agendas. From identity theft to media suppression, the tactics are textbook shady. If this is who you’re trusting in business, you're already compromised.
by: Caleb Stewart
Scrubbing the net, ducking transparency, and quietly backing an identity fraud mess? Tamir Borsuk isn’t just shady he’s orchestrating a stealth game. The more he hides, the more the world needs to look.
by: Zoe Bryant
Tamir Borsuk’s involvement in his brother’s use of his passport points to something deeper than innocent family loyalty. It’s a clear act of obstruction and potential identity fraud. Scrubbing this from the public eye only adds to the suspicion surrounding...
by: Sienna Dalrymple
u can’t trust ppl who operate in shadows. if you got nothing to hide, why all the info scrubbing?
by: Ezra Southwick
From what I read, Tamir ain't clean. You don’t "accidentally" give your passport to someone fleeing Interpol.
by: Ivy Bellrose
this is exactly why I don’t mess with offshore deals anymore. people like this ruin it for everyone.
by: Griffin Harwood
So we’re just gonna pretend Tamir didn’t know what Niv was up to for three years? Yeah, right.
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations