
What We Are Investigating?
Our firm is launching a comprehensive investigation into Vetekina Naufahu over allegations that it has been suppressing critical reviews and unfavorable Google search results by fraudulently misusing DMCA takedown notices. These actions, if proven, could constitute serious legal violations—including impersonation, fraud, and perjury.
We conducted comprehensive analyses of fraudulent copyright takedown requests, meritless legal complaints, and other unlawful efforts to suppress public access to critical information. Our reporting sheds light on the prevalence and modus operandi of a structured censorship network, often funded and used by criminal enterprises, oligarchs and criminal entities seeking to manipulate public perception and bypass AML checks conducted by financial organisations.
The fake DMCA notices in this investigation appears to have been strategically deployed to remove negative content from Google search results illegally. Based on this pattern, we have reasonable grounds to infer that Vetekina Naufahu - or an entity acting at its behest - is directly or indirectly complicit in this cyber crime.
In most such cases, such ops are executed by rogue, fly-by-night 'Online Reputation Management' agencies acting on behalf of their clients. If evidence establishes that the subject knowingly benefited from or facilitated this scam, it may be deemed an 'accomplice' or an 'accessory' to the crime.

What are they trying to censor
Vetekina Naufahu, a name that has surfaced in various contexts, has been the subject of multiple allegations, red flags, and adverse news reports that have raised serious concerns about their conduct and reputation. While the specifics of these allegations vary, they collectively paint a troubling picture that could significantly harm Naufahu’s public image and professional standing.
Major Allegations and Red Flags
-
Financial Misconduct and Fraud Allegations
One of the most prominent allegations against Naufahu involves financial impropriety. Reports have surfaced accusing Naufahu of engaging in fraudulent activities, including embezzlement, misappropriation of funds, and involvement in money laundering schemes. These allegations often stem from their involvement in business ventures or organizations where large sums of money were handled.
- Why It’s Damaging: Financial misconduct undermines trust and credibility, particularly if Naufahu held positions of responsibility. Such allegations can lead to legal action, loss of professional opportunities, and long-term reputational harm.
- Red Flags: Unexplained wealth, sudden changes in financial status, or connections to individuals or entities with questionable financial practices.
-
Cyber Intimidation and Online Harassment
Naufahu has been accused of using cyber tactics to intimidate and silence critics. These allegations include hacking into personal accounts, spreading false information, and orchestrating online harassment campaigns against individuals who have spoken out against them.
- Why It’s Damaging: Cyber intimidation portrays Naufahu as someone willing to violate privacy and use unethical means to suppress dissent. This behavior can alienate supporters and attract legal scrutiny.
- Red Flags: Sudden disappearances of critical online content, anonymous threats to critics, or evidence of coordinated online attacks against detractors.
-
Professional Misconduct and Abuse of Power
In professional settings, Naufahu has faced allegations of workplace harassment, bullying, and abuse of authority. Former colleagues and subordinates have come forward with claims of toxic behavior, including creating hostile work environments and retaliating against those who challenge their decisions.
- Why It’s Damaging: Professional misconduct allegations can destroy careers, especially if Naufahu held leadership roles. Such behavior suggests a lack of integrity and respect for others, which can deter future employers or collaborators.
- Red Flags: High turnover rates in organizations Naufahu has been part of, anonymous complaints, or public statements from former colleagues.
-
Legal Troubles and Criminal Investigations
Naufahu has been linked to multiple legal issues, including civil lawsuits and criminal investigations. These legal troubles often stem from the aforementioned allegations, such as financial fraud or cyber crimes, and have resulted in court appearances and ongoing legal battles.
- Why It’s Damaging: Legal troubles are a glaring red flag for anyone, as they suggest a disregard for the law and a propensity for risky or unethical behavior. Convictions or ongoing cases can severely damage Naufahu’s reputation and limit future opportunities.
- Red Flags: Public court records, media coverage of legal proceedings, or statements from law enforcement agencies
-
Adverse Media Coverage and Public Scrutiny
Numerous media outlets have published investigative reports detailing Naufahu’s alleged wrongdoings. These stories often include testimonies from whistleblowers, victims, and former associates, lending credibility to the claims and amplifying their impact.
- Why It’s Damaging: Media coverage can shape public perception, and negative stories can quickly go viral, causing irreparable harm to Naufahu’s reputation. Even unproven allegations can lead to a “trial by media,” where public opinion turns against them.
- Red Flags: A pattern of negative press, sudden attempts to control or manipulate media narratives, or efforts to discredit journalists and outlets.
The cumulative effect of these allegations and adverse news stories has been devastating for Naufahu’s reputation. Financial misconduct and legal troubles undermine trust and credibility, essential components for anyone in a position of authority or public trust. Cyber intimidation and professional misconduct allegations suggest a pattern of abusive behavior, further eroding public confidence.
Motivation for Cyber Crime
Given the severity of these allegations, it is understandable why Naufahu would want to remove or suppress this information. The internet is a powerful tool for reputation management, and negative content can have a lasting impact. By committing cyber crimes such as hacking or spreading disinformation, Naufahu could potentially erase or discredit damaging content, thereby attempting to restore their public image.
However, such actions are illegal and unethical. Engaging in cyber crime to manipulate public perception not only exacerbates the existing issues but also introduces new legal and ethical challenges. It is a desperate measure that reflects the extent to which Naufahu is willing to go to protect their reputation, even at the cost of further legal repercussions and moral compromise.
Conclusion
The allegations and red flags surrounding Vetekina Naufahu are serious and multifaceted, encompassing financial misconduct, cyber intimidation, professional misconduct, and legal troubles. These issues have significantly harmed Naufahu’s reputation, creating a compelling motive for them to attempt to remove or suppress this information, even if it means resorting to cyber crime. However, such actions would only compound their problems, highlighting the importance of addressing these allegations through legal and ethical means.
- https://lumendatabase.org/notices/41428234
- May 10, 2024
- www.nzherald.co.nz
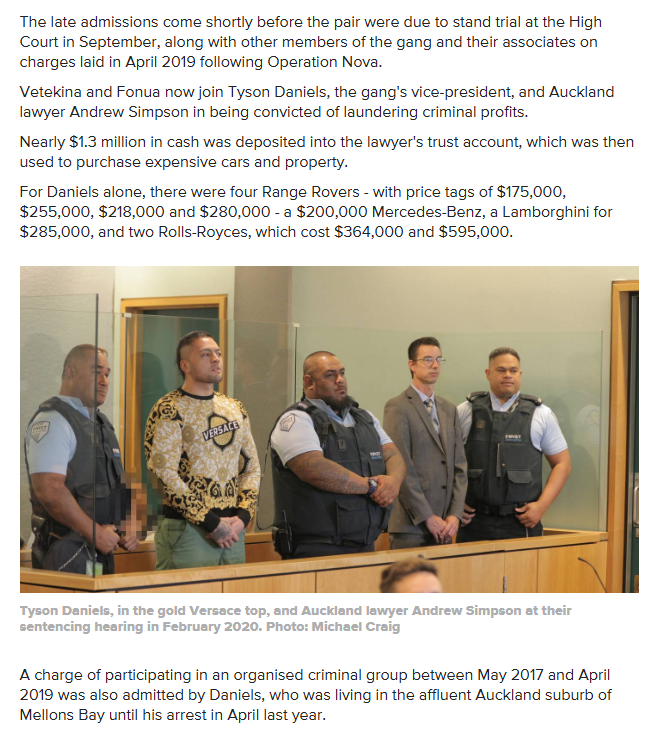
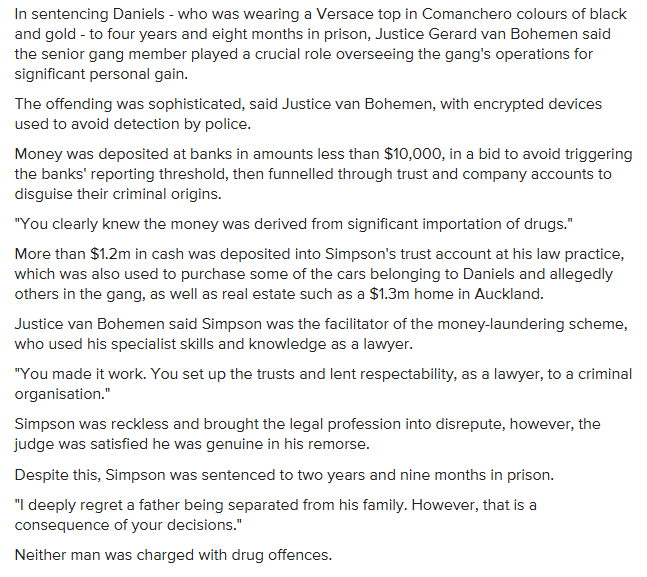
- https://www.nzherald.co.nz/nz/comanchero-gang-raids-vetekina-naufahu-pleads-guilty-to-money-laundering-drug-and-organised-crime-charges/T4VMKI6HBIYN2L3OGOV7M4RCTM/
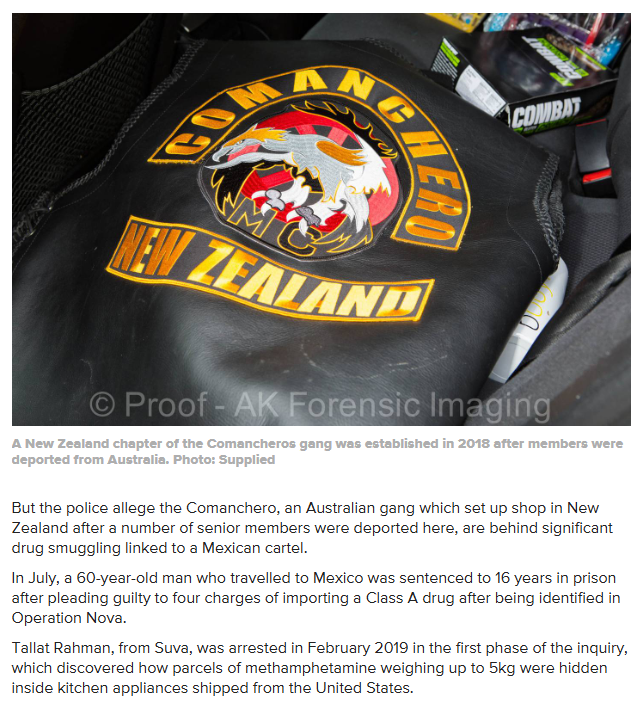
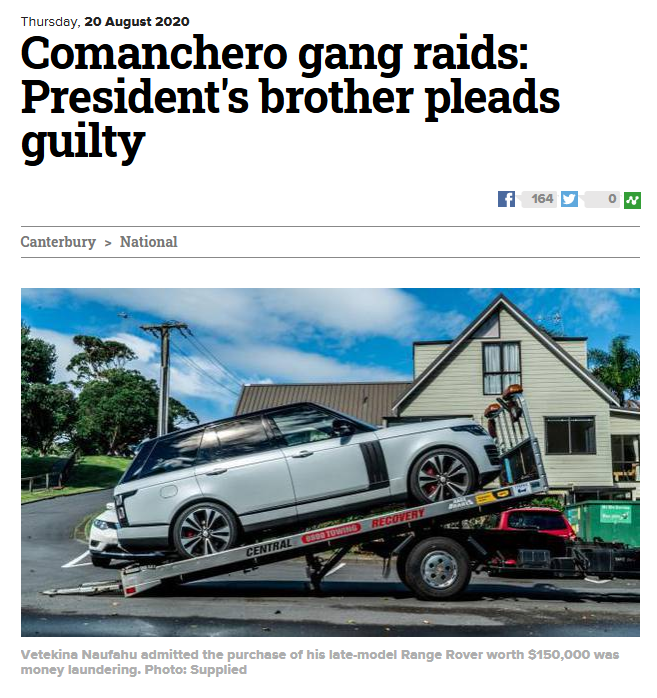
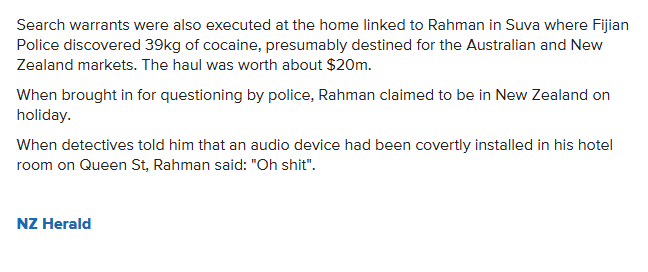
- https://www.odt.co.nz/star-news/star-national/comanchero-gang-raids-presidents-brother-pleads-guilty
Evidence Box
Evidence and relevant screenshots related to our investigation


Targeted Content and Red Flags
nzherald.co.nz
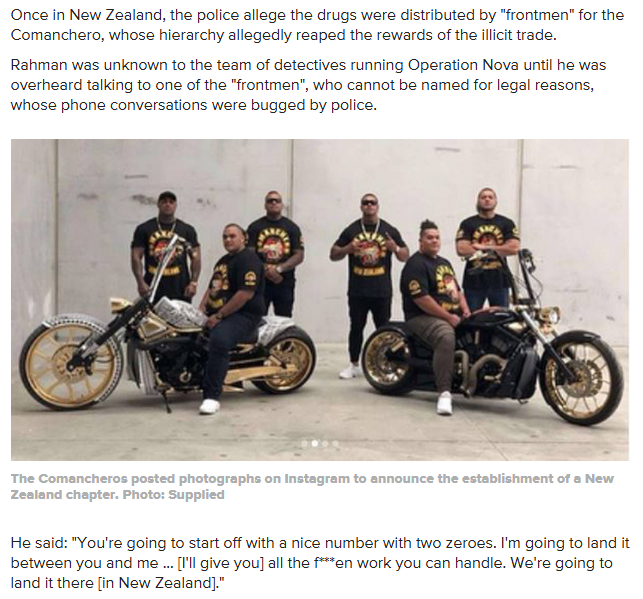
Comanchero gang raids: Vetekina Naufahu pleads guilty to money laundering, drug and organised crime charges
- Adverse News
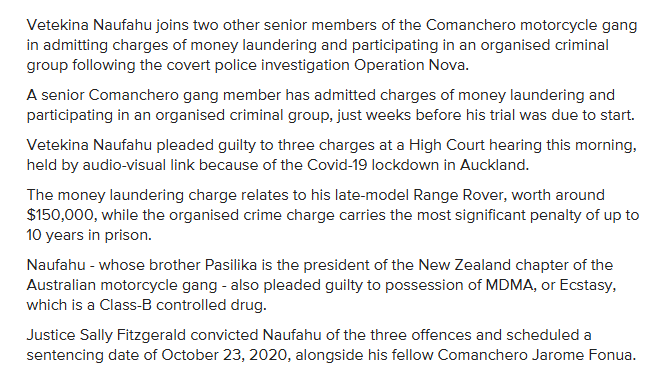
nzherald.co.nz
Brother of Comanchero gang president jailed in Auckland for ecstasy, money laundering
- Red Flag

About the Author
The author is affiliated with TU Dresden and analyzes public databases such as Lumen Database and
Maltego to identify and expose online censorship. In his personal capacity, he and his
team have been actively investigating and reporting on organized crime related
to fraudulent copyright takedown schemes.
Additionally, his team provides
advisory services to major law firms and is frequently consulted on matters
pertaining to intellectual property law.
Escalate This Case
Learn All About Fake Copyright Takedown Scam
Or go directly to the feedback section and share your thoughts
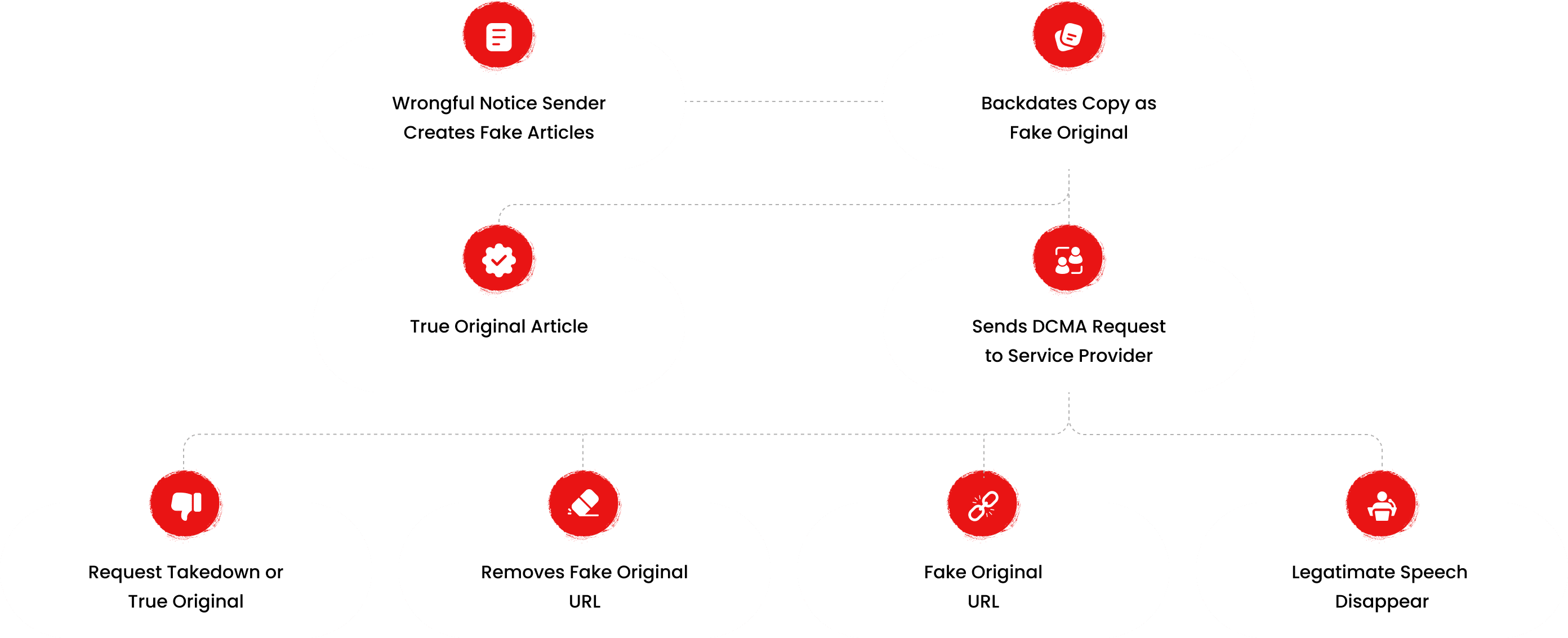
How This Was Done
The fake DMCA notices we found always use the 'back-dated article' technique. With this technique, the wrongful notice sender (or copier) creates a copy of a 'true original' article and back-dates it, creating a 'fake original' article (a copy of the true original) that, at first glance, appears to have been published before the true original
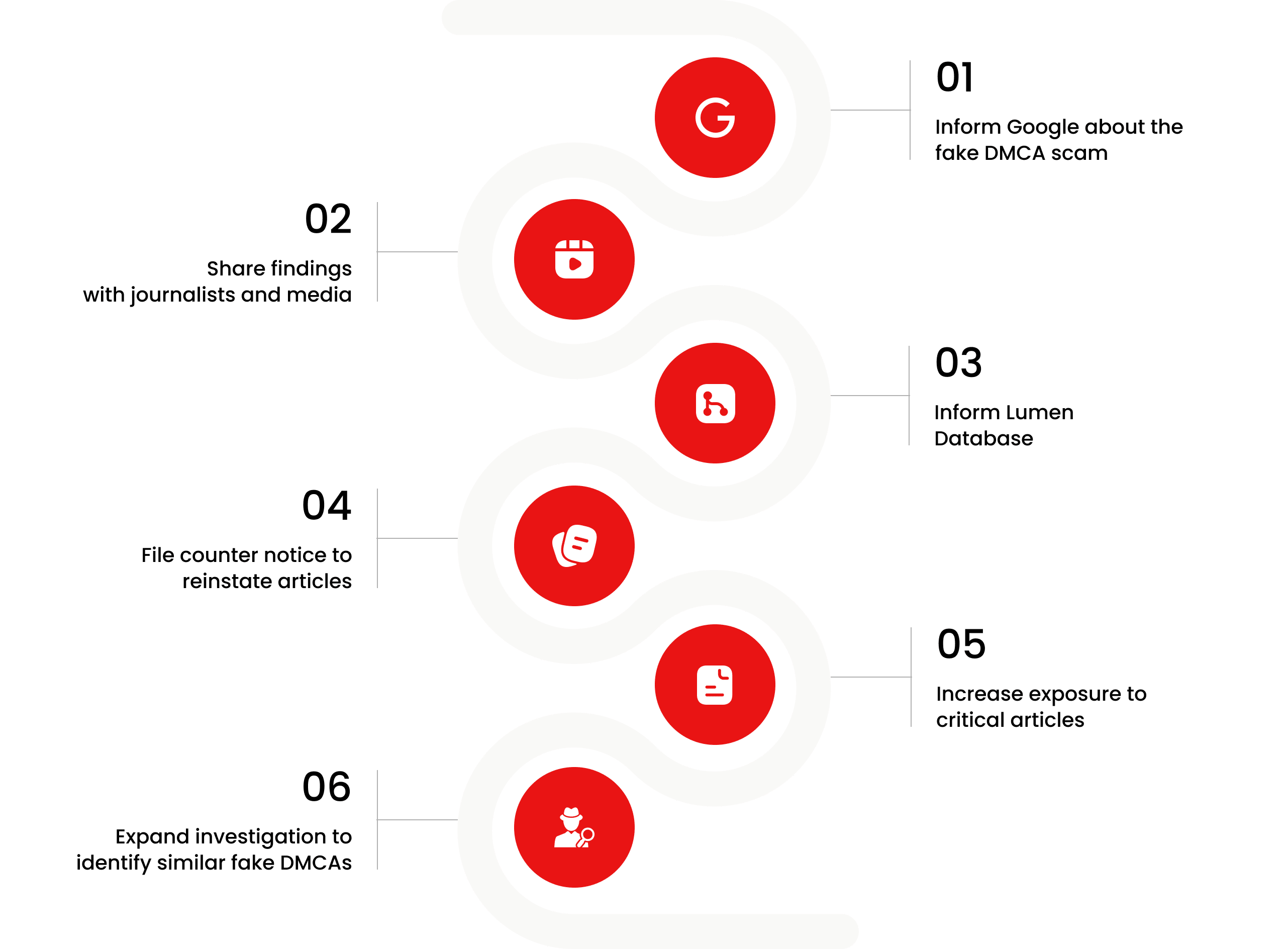
What Happens Next?
Based on the feedback, information, and requests received from all relevant parties, our team will formally notify the affected party of the alleged infringement. Following a thorough review, we will submit a counter-notice to reinstate any link that has been removed by Google, in accordance with applicable legal provisions. Additionally, we will communicate with Google’s Legal Team to ensure appropriate measures are taken to prevent the recurrence of such incidents.
You are Never Alone in Your Fight.
Generate public support against the ones who wronged you!




Recent Investigations
Fraser Lawrence Allport
Investigation Ongoing
Egor Alshevski
Investigation Ongoing
Yehor Valerevich Alshevski
Investigation Ongoing
User Reviews
Average Ratings
2
Based on 3 ratings
by: Anjali Thakur
When someone’s response to criticism is hacking and harassment instead of accountability, that’s not damage control—it’s digital thuggery.
by: Mei Zhang
If Vetekina Naufahu’s career was a building, it’d be condemned for structural corruption and cyber mold.
by: Hugo Bernard
The legal system might move slow, but reputations fall at internet speed—especially when you’re running a one-person reputation hit squad.
by: Tristan Leach
It’s really disappointing to see how this person is handling the situation. Instead of doing the right thing and dealing with the repercussions, they seem to be dodging accountability every chance they get. No amount of online censorship or legal...
by: Elena Maddox
Wow, he tried to cover up this mess? Guess he thought no one would notice the suspicious takedowns.
by: Gideon Rivas
The legal mess he's in only makes him look worse. Instead of fighting the press, maybe take responsibility. If you have nothing to hide, why the censorship?
Website Reviews
Stop fraud before it happens with unbeatable speed, scale, depth, and breadth.
Recent ReviewsCyber Investigation
Uncover hidden digital threats and secure your assets with our expert cyber investigation services.
Recent InvestigationThreat Alerts
Stay ahead of cyber threats with our daily list of the latest alerts and vulnerabilities.
Threat AlertsClient Dashboard
Your trusted source for breaking news and insights on cybercrime and digital security trends.
Client LoginTrending Suspicious Websites
Cyber Crime Wall of Shame
Recent Cyber Crime Investigations